Introduction: Mirai Malware attack on IoT devices
The rise of Internet of Things (IoT) devices, like Internet-connected cameras used in CCTV surveillance, has introduced new vulnerabilities to both personal and business environments.
With attackers exploiting the inadequate security measures typically associated with IoT devices, traditional antivirus and legacy security solutions fall short. To address this critical gap, Darktrace’s Cyber AI Platform provides advanced protection for these increasingly essential yet vulnerable technologies.
Attack Overview: Mirai Malware
In late May, Darktrace detected the Mirai malware infecting an internet-facing DVR camera owned by a logistics company in Canada.
Mirai, first discovered in 2016, continuously scans the Internet for the IP addresses of vulnerable devices in the Internet of Things (IoT), and then turns these devices into bots that can be used as part of botnets for large-scale network attacks. These attacks are often difficult to detect, as IoT devices seamlessly integrate into digital infrastructure, creating a vastly expanded attack surface for organizations.
By drawing on a bespoke, evolving understanding of what is normal for the network, Darktrace caught each stage in this attack’s lifecycle. However, because this company was still conducting their 30-day Proof of Value, Darktrace's Autonomous Response was not in active and the attack continued past the point of initial compromise. Had Darktrace's Autonomous Response been in active mode, the attack would not have advanced past initial compromise.
Attack Timeline

Technical analysis
At the time of the initial breach, this specific botnet’s infrastructure was not yet known to open source intelligence (OSINT). Darktrace, however, detected an EXE download from a location not previously visited by the network.
After the first anomalous EXE download, another was downloaded approximately twenty minutes later. The malware then reached out to multiple IP addresses that were statistically rare for the network. Specifically, the compromised device began transferring large amounts of data to an IP address in China.
Darktrace, by leveraging machine learning algorithms in a protocol agnostic capacity, analyzed this individual device’s transfers within the context of a continuously evolving understanding of what is normal both for this device and for the wider organization. It was therefore able to immediately flag all of these transfers as unusual.
This activity was fully investigated and reported on by Darktrace’s Cyber AI Analyst. A sample of the AI Analyst’s report is shown below. The Suspicious File Download, the Unusual Repeated Connections, and the Unusual External Data Transfer are all presented as unexpected events that call for further investigation. The destination IP of the suspicious download was determined to have 100% hostname rarity relative to what is normal for the organization.

Moreover, the hash of the file, highlighted in a red box in the figure above, revealed that it was a well-known file related to the Mirai Botnet. However, with no antivirus or other security defending the IoT camera, this had gone undetected.
A one-click analysis of the infected device shows a timeline of the model breaches that occurred and graphs the activity to give the report’s readers a quick understanding of the successive stages of the attack. Here, we see the second and third stages of the attack’s lifecycle, in which it starts DDoS against other devices in order to complete its mission while simultaneously continuing outgoing connections to rare destinations in order to sustain its presence.

Conclusion
Interestingly, the client saw no indicators of this activity beyond a sluggish network. This change in network activity was only explained after being identified by Darktrace. Once the client was promptly notified, the compromise was deescalated, and discovering it was a DVR security camera, the client took the device offline.
As this customer was still concluding their trial deployment, Darktrace was not in full autonomous mode. However, if it had been, Darktrace would have responded with a two-tiered action to prevent the device from communicating with the malicious endpoint, cutting the compromised connection before the attack had gained its foothold.

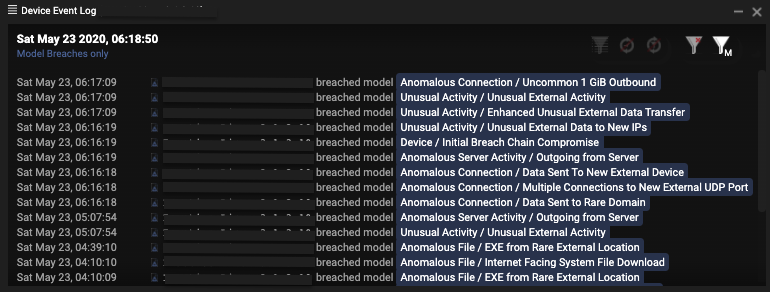
Darktrace model breaches:
- Anomalous Connection / Uncommon 1GiB Outbound
- Unusual Activity / Unusual External Activity
- Unusual Activity / Enhanced Unusual External Data Transfer
- Unusual Activity / Unusual External Data to New IPs
- Device / Initial Breach Chain Compromise
- Anomalous Server Activity / Outgoing from Server
- Anomalous Connection / Data Sent to New External Device
- Anomalous Connection / Multiple Connections to New External UDP Port
- Anomalous Connection / Data Sent to Rare Domain
- Anomalous File / EXE from Rare External Location
- Anomalous File / Internet Facing System File Download

















