Context-aware email defense, beyond just the inbox
Secure your entire messaging ecosystem with AI-driven email security that catches the threats other solutions miss.

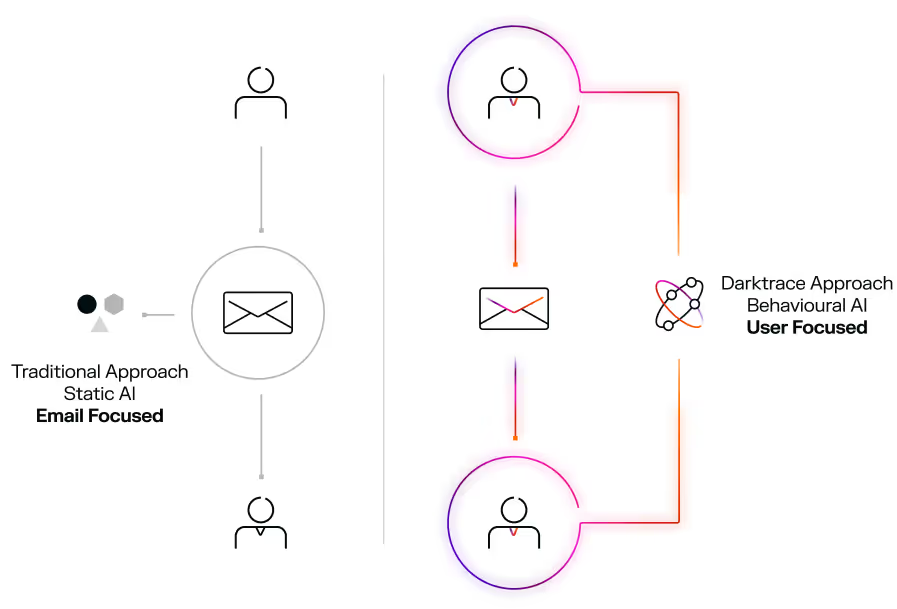
AI is enabling targeted, multi-domain attacks at scale
Revolutionize your email security with Self-Learning AI, defending advanced and novel threats in your inbox and beyond.

Behavioral threat detection stops more threats, faster
Enhance your native email security with Self-Learning AI that understands your business to stop known and unknown threats, without relying on threat intelligence feeds.
While other solutions rely on a first victim to extract IOCs and update threat intelligence databases, Darktrace / EMAIL brings unparalleled security through adaptive, business-centric anomaly detection – so you’ll never be patient zero.
Unlike solutions that rely on historical attack data or limit their focus to either attacker or internal user behavior, Darktrace assumes a zero trust posture and treats every interaction as a potential risk. Self-Learning AI detects novel threats and coordinated campaigns an average of 13 days before leading SEGs.
When a communication arrives, the AI analyzes thousands of data points and asks: Does this message belong here? If the message is normal, it flows through uninterrupted. If it’s suspicious, Darktrace can take a range of actions, from tagging it to full quarantine.
Your email prover already offers a foundational level of security that stops basic threats. Darktrace adds a deeper layer of security that combines this attack-centric approach with a behavior-centric filter tailored to your specific business. These complementary layers add up to a complete defense without any overlapping costs or additional maintenance effort – allowing you to stop the 55% of malicious emails that evade the native email provider when analyzing our customer base.
Evaluate in your environment today
Secure your entire communication surface, wherever you share data
Darktrace prevents threats across inbound, outbound, lateral mail, and account-based, and messaging attacks – removing the need for siloed tools and manual correlation.
Traditional DLP solutions are dictated by a series of rigid policies that depend on rigid policies or labelled data. Our modern DLP solution uses AI-driven behavior and content analysis to detect sensitive information without labels (including PII), preventing accidental and malicious data loss.
Analyze employee-to-employee mailflow and correlate unusual behavioral indicators to determine account compromise, insider threat, or social engineering among employees that could signal an emerging attack.
Darktrace identifies subtle anomalies in user behavior, such as unusual login patterns and administrative activity, to catch when an account has been compromised and taking action to stop it being used as a springboard for sophisticated threats like session token misuse, adversary-in-the-middle attacks, and credential theft.
Darktrace applies the same AI analysis of intent, content, and context to every Teams chat, to detect social engineering and attacks with and without payloads – including pre-texting, novel payloads and zero-days.
Correlate signals across email, identity, and SaaS to reveal the full scope of every attack, allowing you to expose full attack chains and stop threats faster.
Reduce human risk and streamline SOC workflows
Empower your analysts and employees with AI-driven triage and contextual guidance, leading to better end-user reporting and reducing investigations in the SOC by 60%.
Decrease the load on your security team by uplifting end users to report fewer false positives by giving Cyber AI Analyst feedback to each employee as they interact with their mail
Darktrace / EMAIL’s Mailbox Security Assistant performs an advanced behavioral browser analysis and can automatically stop malicious intent hidden within interactive and dynamic web pages that other security tools miss
Centralize and streamline analysis for investigations with Darktrace / EMAIL's live view, combining intuitive search, Cyber AI Analyst reports, and mobile application access

Reduce human risk and streamline SOC workflows


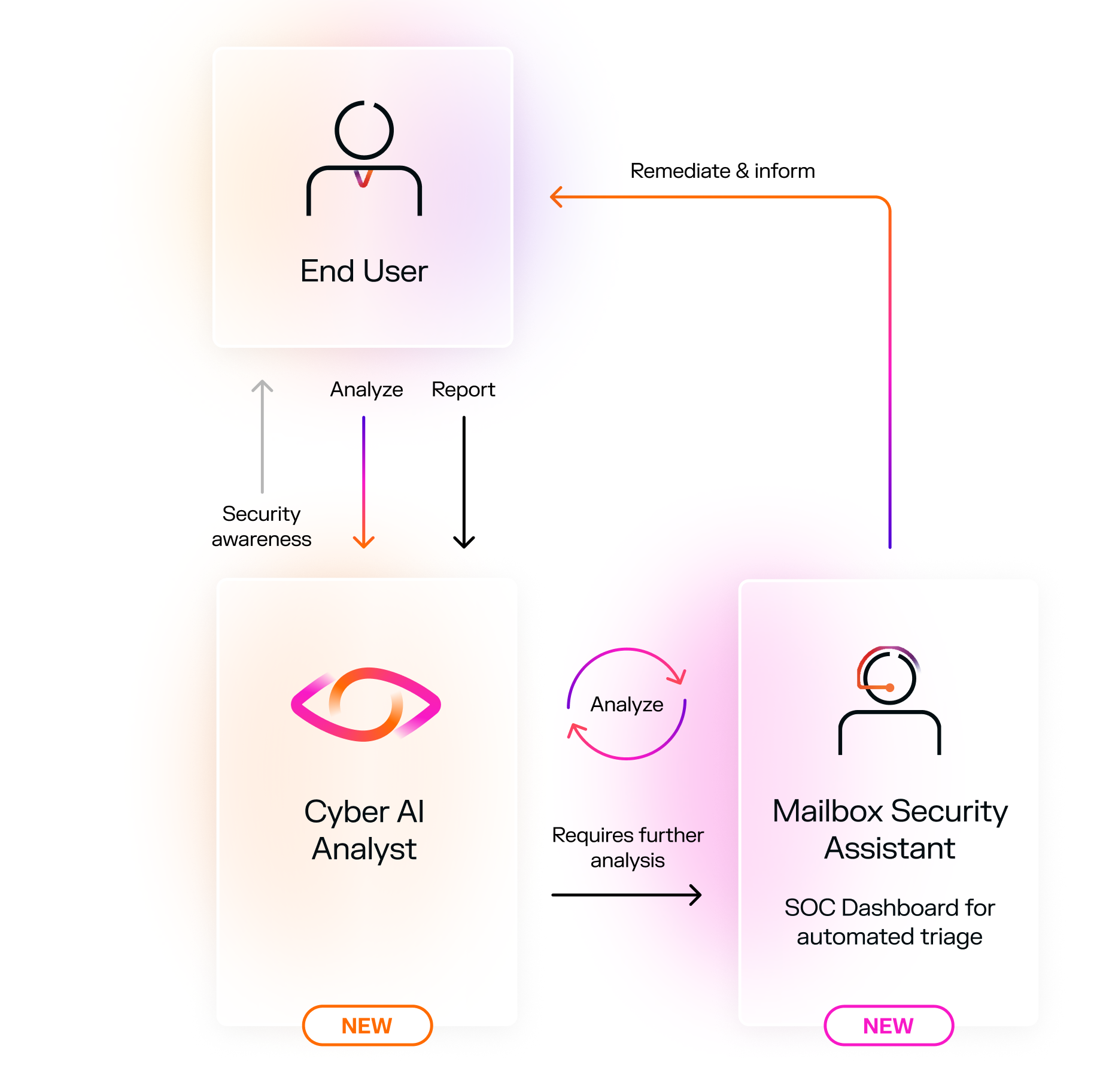
1) A user receives a suspicious email. They can click "Analyze" to see an Al analysis narrative explaining why it has been flagged, building their confidence and improving reporting quality.

2) lf they report the email, Cyber Al Analyst kicks off a deeper investigation -sandboxing Links, correlating recent emails, and identifying

3) lf the email requires further analysis, it flows into the Mailbox Security Assistant, A SOC dashboard for review and action. Analysts can remediate directly from the dashboard. No ticketing, no delays - it's fast, transparent, and built for scale.

Reduce human risk and streamline SOC workflows
Empower your analysts and employees with AI-driven triage and contextual guidance, leading to better end-user reporting and reducing investigations in the SOC by 60%.
Stage 1


Stage 2
Stage 3

Calculate your
potential ROI
Discover the ROI potential you could achieve with Darktrace / EMAIL, alongside powerful security benefits.

Data Loss Prevention
Complete data loss prevention across all outbound mail
Teams
Extend email protection to messaging
DMARC
Accessible DMARC to protect your brand
Better Together
Darktrace and Microsoft have partnered to help organizations close the security gaps in their multi-cloud and multi-platform environments. Darktrace / EMAIL, hosted on Microsoft Azure, integrates with both Microsoft 365 and Microsoft Exchange.

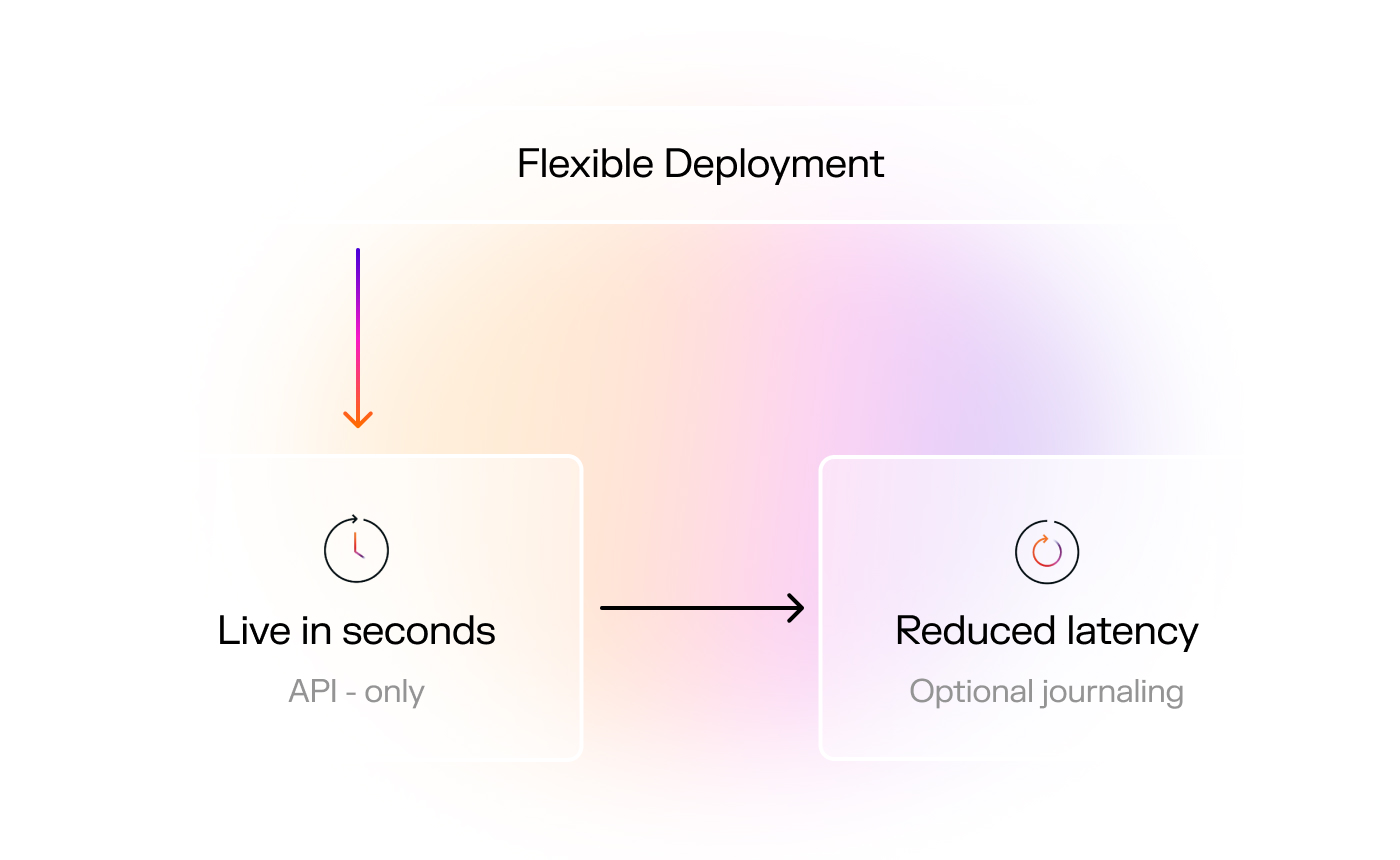
Fast deployment, according to your needs
Whether you choose API-only or API plus journaling, Darktrace deploys 30x faster than other solutions – with no disruption to mail flow. And say goodbye to weekly maintenance with AI that continuously adapts to each end-user.
See Darktrace / EMAIL in action
Watch the video demo to see how Darktrace provides defense-in-depth across the full spectrum of email threats.
Frequently asked
questions
Email threat protection refers to the suite of tools and technologies designed to safeguard email communications from a wide range of cyber threats. As email remains one of the most common attack vectors, email threat protection is crucial in defending against phishing, malware, business email compromise (BEC), and other sophisticated tactics used by cybercriminals.
As email-based cyberattacks grow more sophisticated, vendors in email threat protection are taking varied approaches to address threats. Many rely on using historical attack data to try and predict what the next threat will look like.
Others are using AI and machine learning to detect novel or targeted threats, such as sophisticated phishing attempts and business email compromise. AI can identify subtle anomalies in email patterns and sender behavior. This focus on behavioral analysis helps defenders detect suspicious account activity and prevent lateral movement within compromised accounts, helping identify threats that exploit trust within organizations.
To tackle multistage and multichannel threats, email security is increasingly integrating protection across platforms like Microsoft Teams or Slack, expanding threat visibility and minimizing attack surfaces beyond email. Advanced solutions also incorporate real-time threat intelligence and sandboxing, allowing them to isolate and analyze potentially malicious content, providing robust defenses against evolving attack vectors.
For data security, some vendors now offer integrated data loss prevention (DLP) and encryption to prevent sensitive information leaks. These features sometimes include automated protection and user training. Additionally, email threat protection sometimes integrates email events into broader security frameworks, such as SIEM and XDR, supporting a comprehensive, organization-wide approach to threat response.
This shift towards more advanced, integrated email security solutions reflects the need for flexible, adaptive protections as communication-based threats continue to evolve in complexity.
The main difference between AI-powered and traditional rule-based email security lies in how they detect threats and adapt. Older rule-based systems (like Secure Email Gateways, or SEGs) work on fixed instructions. They flag emails based on a list of known malware signatures, blocked senders, or specific keywords. This checklist approach creates a static defense that requires exact knowledge of every threat characteristic to be effective. Because of this, these systems can only respond to known threats, meaning they fall behind threat actors who are constantly evolving their tactics.
Plus, managing large sets of manually updated rules places a significant burden on security operations center (SOC) teams, which can lead to misconfigurations and miss the subtle changes in an organization's communication patterns.
Conversely, AI-powered email security can transform defense by constantly learning an organization's unique "pattern of life." These multi-layered AI solutions automatically build a moving picture of normal behavior for every user. The AI studies content themes, attachment types, and even writing styles.
This technology continuously processes data to identify any deviation from the usual pattern that could indicate possible sign of compromise. As a result, these tools can proactively detect highly targeted spear phishing, advanced impersonation attempts, and supply chain attacks that closely resemble genuine communications.
The unsupervised machine-learning approach ensures security continuously adjusts without constant human input, providing stronger protection against new threats with no existing signatures. It shifts the focus from knowing every attack to understanding and protecting your organization's unique digital identity, significantly improving resilience against advanced persistent threats and lowering the risk of a breach.
When choosing an email security solution for a cloud-based platform like Microsoft 365, select a tool that integrates deeply and smoothly with Microsoft 365's architecture, ideally using API-level connectivity. This setup is better than relying solely on traditional mail flow rules, as it provides complete visibility into internal email traffic and helps detect attacks spreading within the organization. Easy integration also means simpler deployment and less work for IT teams.
Choose an email security platform that provides protection that enhances and extends Microsoft 365's built-in features. Modern threats, such as zero-day exploits, highly personalized spear phishing, and advanced impersonation attacks, are constantly evolving. The chosen security technology should have capabilities such as AI-powered anomaly detection. This adaptive intelligence adds an essential layer on top of Microsoft 365 security for defending against the most dangerous, targeted attacks that exploit human trust.
Ensure the tool secures email across its entire journey. It should cover outgoing messages to prevent data loss or brand impersonation. It should also include internal emails to stop threats from spreading after a user is compromised. Effective post-delivery remediation is also essential. The system should allow for quick detection, quarantine, or removal of compromised emails to minimize exposure time and reduce manual effort for SOC teams.
Finally, check that your chosen email security tool does not double up on your Microsoft 365 native security or require it to be disabled. An email security tool should build on Microsoft E5 capabilities rather than replacing them, duplicating cost and workflows.
Ultimately, email security software should make a security team's job easier, not harder. The technology should accurately detect real threats and reduce the number of false alarms. This directly improves the efficiency of security teams, letting them focus on important issues rather than sifting through irrelevant alerts.
The rapid evolution of cyberattacks has exposed key vulnerabilities in email security that businesses must address to safeguard their data effectively:
• Detecting AI-Driven Threats: Traditional email security systems often fall short against highly sophisticated attacks, such as AI-driven phishing schemes, deepfake impersonations, and advanced social engineering. These threats leverage advanced personalization, making them harder to detect with rule-based methods. Advanced email security solutions now integrate AI to detect unusual patterns and suspicious behaviors that could indicate such AI-driven attacks.
• Mitigating Supply Chain Vulnerabilities: Cybercriminals are increasingly exploiting trusted relationships within supply chains, using compromised vendors or partners as entry points for lateral attacks. This makes it challenging for organizations to detect account takeovers that move through the supply chain. Modern email security products address this by tracking sender reputation and analyzing connection behaviors across accounts to identify and mitigate these risks.
• Countering Evasive and Morphing Malware: Today’s malware evolves continuously, adapting its structure to bypass static defenses. To combat this, email security solutions are now incorporating real-time threat intelligence, behavioral analysis, and sandboxing. These tools detect changes in malware signatures and isolate suspicious attachments or links before they reach users, effectively countering the evasive nature of modern malware.
• Handling Complex, Multistage Payloads: Cyber-attackers are embedding payloads in novel forms, like QR codes or hidden URLs, creating complex, multistage attack chains that are harder to detect. Email security solutions must now go beyond basic text and attachment scans to identify unconventional payloads, ensuring they analyze and block any element that could contain malicious code.
• Securing a Broader Attack Surface: As communication extends to platforms beyond email, such as messaging tools like Teams or Slack, organizations face an expanded attack surface. Comprehensive email security products now integrate with these additional platforms, providing unified protection across multiple channels, which is crucial for preventing lateral threats and maintaining data security.
By addressing these evolving attack vectors, modern email security solutions provide businesses with robust, multi-layered protection against data breaches and unauthorized access, enabling them to defend against increasingly sophisticated cyber threats.
The time it takes to deploy and configure email security systems depends on several factors, including the type of tool chosen and the complexity of the organization. Generally, the timeline includes initial setup, configuration, and an observation or learning period.
For older, gateway-based systems, deployment can take weeks or months. The longer time frame results from significant changes to network settings, like adjusting DNS records to redirect all email traffic through the new security appliance. This process requires careful coordination with network teams and thorough testing to ensure mail flow isn't interrupted. Then comes the manual configuration of numerous rules and policies, which can be a very time-consuming process, especially for larger organizations with diverse communication needs.
However, modern AI-powered email security solutions deliver a significantly faster deployment experience. Most modern technology integrates via APIs, connecting directly to your email service without needing to reroute mail or implement complex network changes. This API-driven approach accelerates the initial setup phase, showcasing how quickly AI can begin securing an environment.
Once connected, these AI systems begin learning immediately. Instead of requiring extensive manual rule-setting, they autonomously start building a detailed picture of your organization's normal email behavior. During the learning period, these tools generally don’t demand active, hands-on configuration from your security team. Their role shifts from intensive manual setup to overseeing and fine-tuning as the AI adapts.
Behavioral analysis involves understanding what "normal" looks like for a particular user, device, or system. Instead of checking emails against a list of rules, it builds a dynamic profile of typical activity. It continuously monitors numerous data points, including who typically emails whom, the usual size and type of attachments, the language used, common sending times, and even the geographic locations from which users access their mail.
By continually learning and establishing a baseline of normal behavior, the system can identify any deviations that suggest potential malicious activity. This approach excels at detecting novel threats, such as zero-day attacks or highly sophisticated spear phishing campaigns that have no known signatures. Since it's looking for abnormal behavior rather than specific threat patterns, it can detect attacks designed to bypass traditional defenses.
For example, say an executive's email suddenly starts sending unusual financial requests to accounting or tries to access sensitive files. Behavioral analysis flags this deviation from their normal pattern, even if the content doesn't contain obvious malware. This analysis can detect subtle impersonation attempts or account takeovers in real time, speeding up containment and response.
Behavioral analysis also enhances contextual awareness, making it more effective at distinguishing between a genuine but unusual email and a truly malicious one. This reduces false positives, allowing SOC teams to focus on genuine threats.
See Darktrace / EMAIL
in action
Watch the video demo to see how Darktrace provides defense-in-depth across the full spectrum of email threats.
































