Prioritize on true cyber risk
Stop cyber risks from becoming reality with cross-stack attack path modeling, threat and vulnerability management, and AI risk assessment that understands your business

As attackers innovate, defenders are
stuck in fire fighting mode
Proactively reduce risk, harden your security posture, and anticipate attacks

Evaluate in your environment today
Understand your unique risk profile
An AI-based risk based scoring system generates unique, specific risk scoring for each business rather than general claims about patch latency or CVE risk.
Top rankings and risk baselines provide an effective, prioritized view for cyber risk discovery and allow you to address the users, devices, and vulnerabilities which pose the most severe compromise risk to your business.
Continuous learning of cyber risk is fed into the detection and response capabilities of the Darktrace ActiveAI Security Platform. Quickly evaluate the potential impact to affected assets during incidents and strengthen response along your most critical attack paths.

This is the default text value
This is the default text value

This is the default text value
This is the default text value

This is the default text value
This is the default text value
Get an adversarial view of your risk
with AI-driven attack path modeling that surfaces exposures across multiple technology domains and human communication factors
Surface human weak points with email phishing engagements designed to test employee susceptibility and enhance awareness training
by mapping the MITRE ATT&CK framework to your business to understand the mitigation steps needed to make them harder to achieve
Empower and mobilize your team
Map the latest APTs and integrate with your other tools to present a transparent view of the most immediate CVE risks facing the business, their impacts, and how to stop them.
Shows your most immediate vulnerability risks, not just in the context of common industry scoring, but an understanding of your unique environment
Minimize exposure before an exploit, with risk-reducing advisories that proactively harden your security posture with tailored advice
Map adversary targeting and attack behaviors to your business profile to give you a better understanding of attack likelihood

Evaluate in your environment today
Proactive Exposure Management: Workflow
The value of a technology depends on how effectively it is used. The recommended workflow for Darktrace / Proactive Exposure Management™ maps to the workflow set out in Gartner’s Continuous Threat Exposure Management (CTEM) structure.
Scope
Understand vulnerable entry points and assets
Darktrace provides an exposure score – a measure of accessibility and interactivity – for every asset. The most exposed devices pose natural starting or pivot points for adversaries.

Discover
Identify active risks
Proactive Exposure Management will continually assess the Impact, Damage, Weakness, Exposure and Difficulty (to compromise) associated with every asset to identify which human or technology assets are most exploitable and could lead to the biggest damage against the business.

Prioritize
Focus on the most important security issues
Top rankings show the users, devices and most damaging CVEs that are present. APTs and MITRE techniques are ranked and placed in the context of your business susceptibly. CVEs display multiple scores (severity, priority, Darktrace vulnerability) to help you decide which to target along with matching advisories that are also ranked. Each of these risks are displayed in a practical format within the attack paths.

Validate
Assess potential pathways
Attack engagements give teams the opportunity to test human risks with real phishing emails sent from internal accounts. Attack path modeling places all risks in context with associated difficulty scores validating the ease with which an attacker can use their desired technique. Darktrace may also be used to augment independent pen-testing efforts.

Mobilize
Action identified risks and communicate to broader stakeholders
Ranked advisories provide a clear opportunity for a structured patching and mitigation plan, and automated risk reporting ensures quick, written summaries of all risks facing a business. A CVE management dashboard includes the consequences of not following appropriate mobilization efforts such as the cost of patch latency.

Reveal, prioritize and remove misconfigurations
Misconfigurations are mapped to attack paths to reveal the true risk each one presents to your business, helping prioritization and remediation

Identify active risks through scanner integration or manual CVE entry
Darktrace ingests vulnerability scanner findings or manual CVE entry to identify your active technology risks.

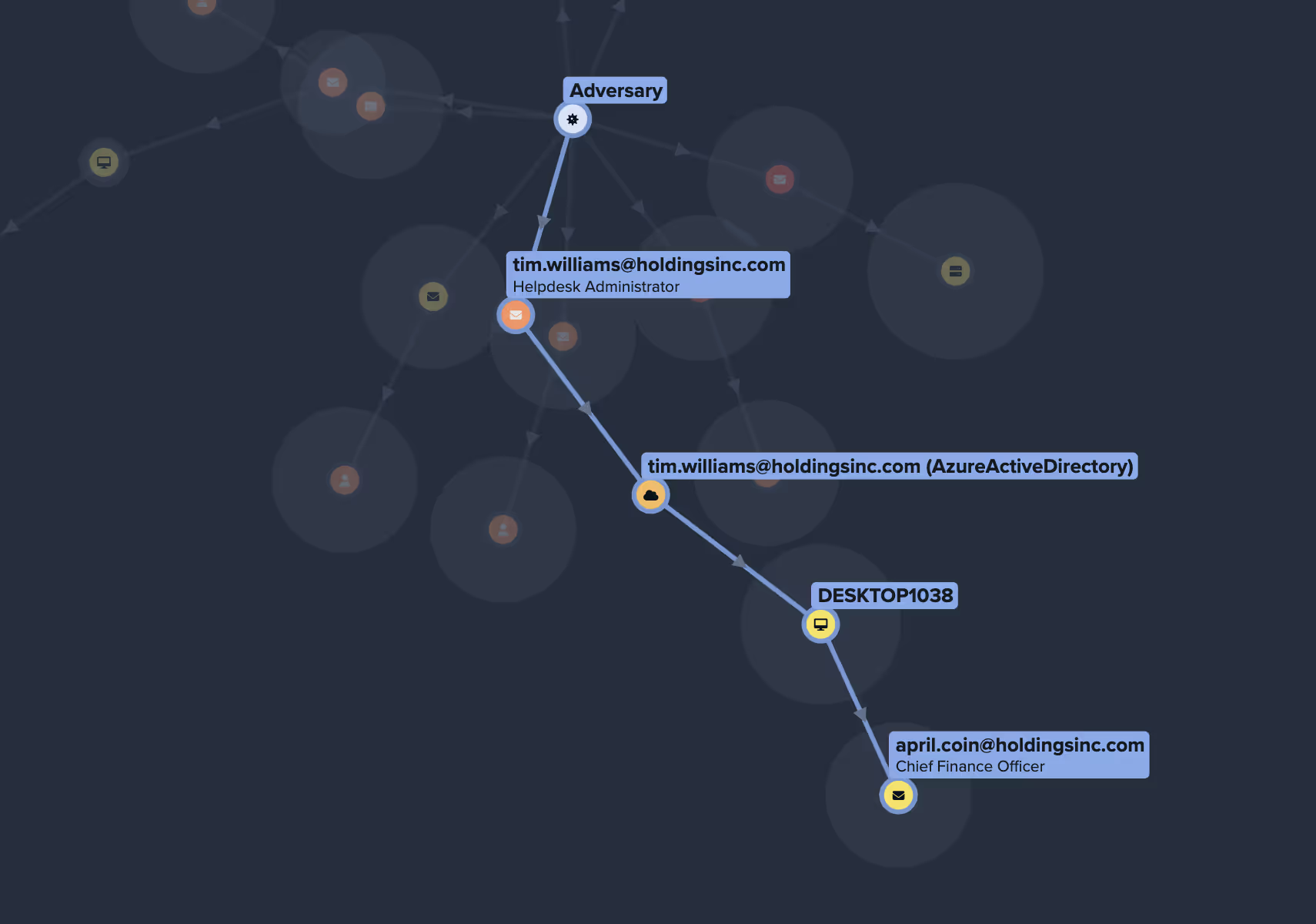
Reveal attack paths missed by simple CVE lists
Reveals complex, multi-stage, potential attack paths across your network, AD, cloud, email accounts, OT, endpoint and the external attack surface.

Assist independent red team duties
Allows pentesters to focus and validate areas with the highest risk – or can be used at end of red teaming process to see what teams might have missed

Reveal the consequences of Shadow IT
Pairs with Darktrace / Attack Surface Management to show unknown relationships and potential attack paths between Shadow IT and approved IT assets. ‘Shadow’ users can also be exposed on attack paths by revealing those users with over-entitled access to unintentional assets.

Read the
solution brief
Discover the unique features and capabilities of Darktrace / Proactive Exposure Management in more detail





































