Priorice el verdadero riesgo cibernético
Impida que los riesgos cibernéticos se hagan realidad con el modelado de rutas de ataque multiplataforma, la gestión de amenazas y vulnerabilidades y la evaluación de riesgos de la IA que entiende tu negocio

A medida que los atacantes innovan, los defensores
atrapado en el modo de extinción de incendios
Reduzca el riesgo de forma proactiva, refuerce su postura de seguridad y anticipe los ataques

Evalúe hoy mismo en su entorno
Comprenda su perfil de riesgo único
Un sistema de puntuación basado en el riesgo basado en la IA genera una puntuación de riesgo única y específica para cada empresa, en lugar de hacer afirmaciones generales sobre la latencia de los parches o el riesgo de CVE.
Las principales clasificaciones y las bases de riesgo proporcionan una visión eficaz y priorizada para el descubrimiento de riesgos cibernéticos y le permiten abordar los usuarios, los dispositivos y las vulnerabilidades que representan el riesgo de compromiso más grave para su empresa.
El aprendizaje continuo del riesgo cibernético se incorpora a las capacidades de detección y respuesta de la Plataforma de seguridad ActiveAI de Darktrace. Evalúe rápidamente el posible impacto en los activos afectados durante los incidentes y refuerce la respuesta en las rutas de ataque más críticas.

This is the default text value
This is the default text value

This is the default text value
This is the default text value

This is the default text value
This is the default text value
Obtenga una visión contradictoria de tu riesgo
con un modelado de rutas de ataque basado en inteligencia artificial que revela las exposiciones en múltiples dominios tecnológicos y factores de comunicación humana
Destape los puntos débiles de las personas con campañas de suplantación de identidad por correo electrónico diseñadas para evaluar la susceptibilidad de los empleados y mejorar la formación de sensibilización
asignando el marco de MITRE ATT&CK a su empresa para comprender los pasos de mitigación necesarios para que sean más difíciles de lograr
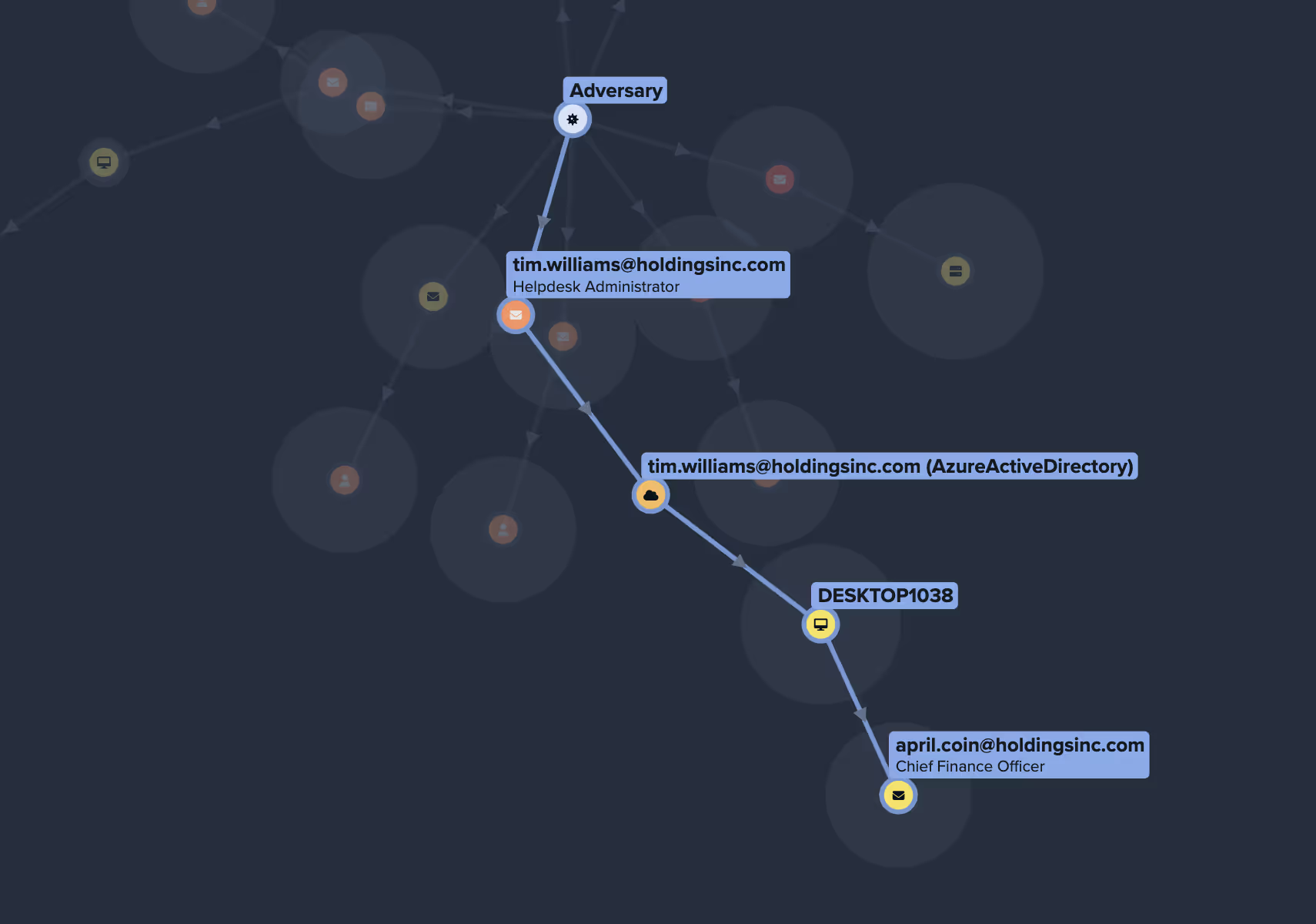
Capacite y movilice a su equipo
Mapee las APT más recientes e intégrelas con sus otras herramientas para presentar una visión transparente de los riesgos de CVE más inmediatos a los que se enfrenta la empresa, sus impactos y cómo detenerlos.
Muestra sus riesgos de vulnerabilidad más inmediatos, no solo en el contexto de una puntuación común del sector, sino también en el contexto de una comprensión de su entorno único
Minimice la exposición antes de que se produzca una vulnerabilidad con avisos de reducción de riesgos que refuerzan de forma proactiva su postura de seguridad con consejos personalizados
Asigne los comportamientos de ataque y segmentación de los adversarios a su perfil empresarial para comprender mejor la probabilidad de ataque

Evaluate in your environment today
Gestión proactiva de la exposición: flujo de trabajo
El valor de una tecnología depende de la eficacia con la que se utilice. El flujo de trabajo recomendado para Darktrace/Gestión Proactiva de la Exposición™ se corresponde con el flujo de trabajo establecido en la estructura de gestión continua de la exposición a amenazas (CTEM) de Gartner.
Alcance
Comprenda los puntos de entrada y los activos vulnerables
Darktrace proporciona una puntuación de exposición (una medida de accesibilidad e interactividad) para cada activo. Los dispositivos más expuestos representan puntos de partida o de pivote naturales para los adversarios.

Descubre
Identificar los riesgos activos
La gestión proactiva de la exposición evaluará continuamente el impacto, el daño, la debilidad, la exposición y la dificultad (de comprometer) asociados a cada activo para identificar qué activos humanos o tecnológicos son más explotables y podrían provocar el mayor daño para la empresa.

Priorizar
Céntrese en los problemas de seguridad más importantes
Las clasificaciones más altas muestran los usuarios, los dispositivos y los CVE más dañinos que están presentes. Las técnicas APT y MITRE se clasifican y colocan en el contexto de su negocio de manera susceptible. Los CVE muestran varias puntuaciones (gravedad, prioridad, vulnerabilidad de Darktrace) para ayudarte a decidir a qué objetivos dirigirte, además de los avisos coincidentes que también están clasificados. Cada uno de estos riesgos se muestra en un formato práctico dentro de las rutas de ataque.

Validar
Evalúe las posibles vías
Los ataques brindan a los equipos la oportunidad de probar los riesgos humanos con correos electrónicos de suplantación de identidad reales enviados desde cuentas internas. El modelado de la ruta de ataque sitúa todos los riesgos en su contexto y las puntuaciones de dificultad asociadas validan la facilidad con la que un atacante puede utilizar la técnica deseada. Darktrace también se puede usar para aumentar los esfuerzos independientes de prueba con lápiz.

Movilizar
La acción identificó los riesgos y los comunicó a las partes interesadas en general
Los avisos clasificados brindan una oportunidad clara para un plan estructurado de parches y mitigación, y los informes de riesgos automatizados garantizan resúmenes rápidos y escritos de todos los riesgos a los que se enfrenta una empresa. Un panel de administración de CVE incluye las consecuencias de no seguir los esfuerzos de movilización adecuados, como el costo de la latencia de los parches.

Revele, priorice y elimine los errores de configuración
Las configuraciones incorrectas se asignan a las rutas de ataque para revelar el verdadero riesgo que cada una representa para su empresa, lo que ayuda a priorizar y corregir

Identifique los riesgos activos mediante la integración de escáneres o la entrada manual de CVE
Darktrace recopila los hallazgos del escáner de vulnerabilidades o la entrada manual de CVE para identificar los riesgos tecnológicos activos.

Revela las rutas de ataque que las simples listas de CVE no detectan
Revela posibles rutas de ataque complejas, de varias etapas y en su red, AD, nube, cuentas de correo electrónico, OT, puntos finales y la superficie de ataque externa.

Ayudar en las tareas del equipo rojo independiente
Permite a los pentésteres centrarse y validar las áreas con mayor riesgo, o se puede utilizar al final del proceso de formación de equipos en rojo para ver qué es lo que los equipos pueden haber pasado por alto

Revele las consecuencias de la TI en la sombra
Se combina con Darktrace/Gestión de Superficies de Ataque para mostrar las relaciones desconocidas y las posibles rutas de ataque entre la TI en la sombra y los activos de TI aprobados. Los usuarios «ocultos» también pueden quedar expuestos a las rutas de ataque al revelar a los usuarios con derechos excesivos de acceso a activos no intencionados.

Lea el
resumen de la solución
Descubra las funciones y capacidades únicas de Darktrace / Gestión Proactiva de la Exposición en más detalles



































