In the realm of Industrial Control System (ICS) security, two concepts often dominate discussions:
- Asset visibility
- Signature-based threat detection
While these are undoubtedly important components of a cybersecurity strategy, many organizations focus on them as the primary means to enhance ICS security. However, this is more of a short-term approach and these organizations often realize too late that these efforts do not translate into actually securing their environment.
To truly secure your environment, organizations should focus their efforts on anomaly detection across core network segments. This shift enables enhanced threat detection, while also providing a more meaningful and dynamic view of asset communication.
By prioritizing anomaly detection, organizations can build a more resilient security posture, detecting and mitigating threats before they escalate into serious incidents.
The shortcomings of asset visibility and signature-based threat detection
Asset visibility is frequently touted as the foundation of ICS security. The idea is that you cannot protect what you cannot see.
However, organizations that invest heavily in asset discovery tools often end up with extensive inventories of connected devices but little actionable insight into their security posture or risk level, let alone any indication as to whether these assets have been compromised.
Simply knowing what assets exist does not equate to securing them.
Worse, asset discovery is often a time-consuming static process. By the time practitioners complete their inventory, not only is there likely to have been changes to their assets, but the threat landscape may have already evolved, introducing new vulnerabilities and attack vectors that were not previously accounted for.
Signature-based detection is reactive, not proactive
Traditional signature-based threat detection relies on known attack patterns and predefined signatures to identify malicious activity. This approach is fundamentally reactive because it can only detect threats that have already been identified elsewhere.
In an ICS environment where cyber-attacks on OT systems have become more frequent, sophisticated, and destructive, signature-based detection provides a false sense of security while failing to detect sophisticated, previously unseen threats:
- 75% of surveyed organizations reporting malicious cyber activity in their OT networks.
- Downtime caused by ransomware attacks alone costing the manufacturing industry $46 billion over the past five years.
- 73% of organizations now reporting intrusions affecting both IT and OT systems, up from 49% in 2023.[3]
Additionally, adversaries often dwell within OT networks for extended periods, studying their specific conditions to identify the most effective way to cause disruption. This means that the likelihood of any attack within OT network looking the same as a previous attack is unlikely.
Implementation effort vs. actual security gains
Many organizations spend considerable time and resources implementing asset visibility solutions and signature-based detection systems only to be required to constantly tune and adjust the sensitivity of the solution.
Despite these efforts, these tools often fail to deliver the level of protection expected, leaving gaps in detection, an overwhelming amount of asset data, and a constant stream of false positives and false negatives from signature-based systems.
A more effective approach: Anomaly detection at core network segments
While it's important to understand the type of device involved during alert triage, organizations should shift their focus from static asset visibility and threat signatures to anomaly detection across critical network segments. This method provides a superior approach to ICS security for several reasons:
Proactive threat detection
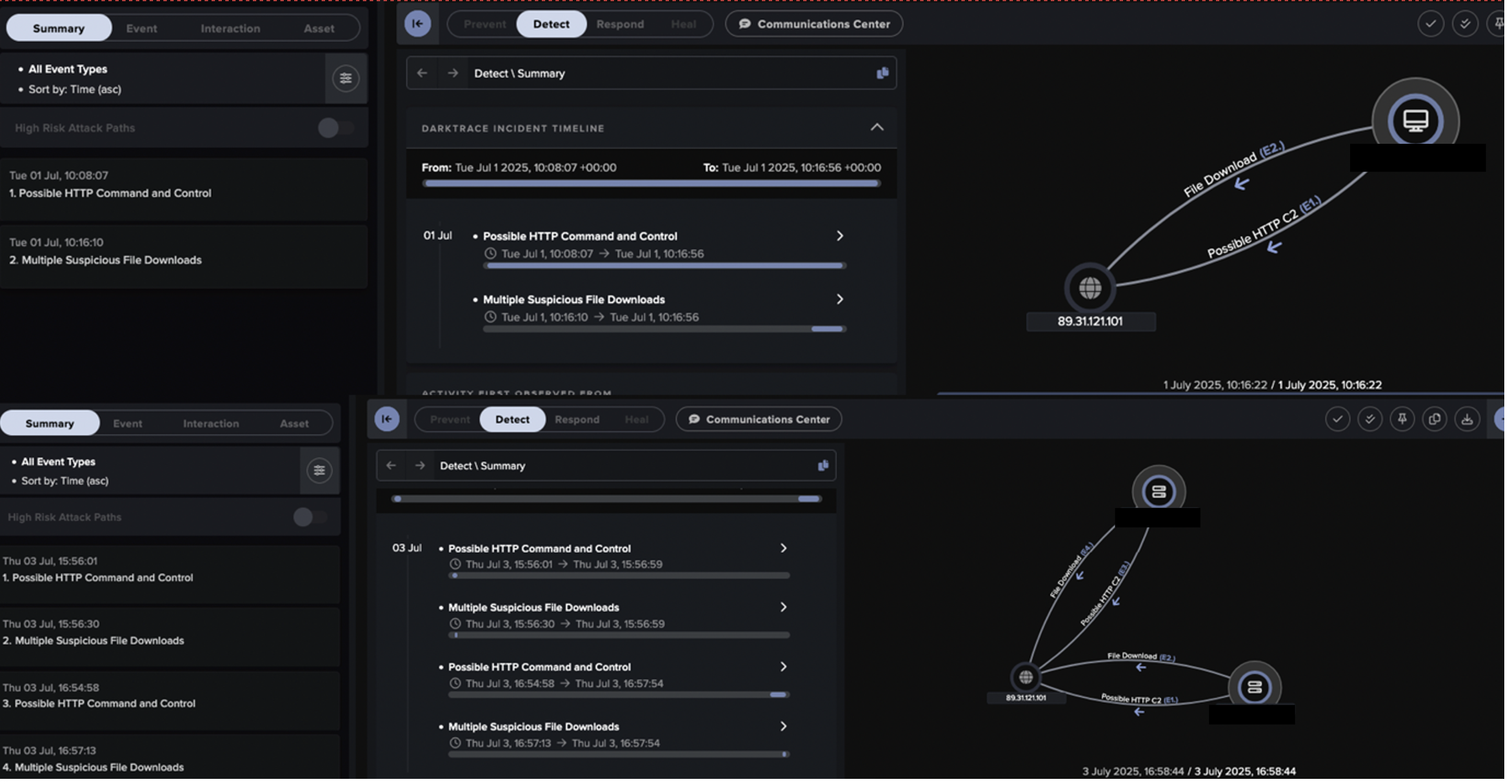
Anomaly detection monitors network behavior in real time and identifies deviations . This means that even novel or previously unseen threats can be detected based on unusual network activity, rather than relying on predefined signatures.
Granular security insights
By analyzing traffic patterns across key network segments, organizations can gain deeper insights into how assets interact. This not only improves threat detection but also organically enhances asset visibility. Instead of simply cataloging devices, organizations gain meaningful visibility into how they behave within the network, understanding their unique pattern of life, and making it easier to detect malicious activity.
Efficiency and scalability
Implementing anomaly detection allows security teams to focus on real threats rather than sifting through massive inventories of assets or managing signature updates. It scales better with evolving threats and provides continuous monitoring without requiring constant manual intervention.
Enhanced threat detection for critical infrastructure
Unlike traditional security approaches that rely on static baselines or threat intelligence that doesn't reflect the unique behaviors of your OT environment, Darktrace / OT uses multiple AI techniques to continuously learn and adapt to your organization’s real-world activity across IT, OT, and IoT.
By building a dynamic understanding of each device’s pattern of life, it detects threats at every stage of the kill chain — from known malware to zero-days and insider attacks — without overwhelming your team with false positives or unnecessary alerts. This ensures scalable protection as your environment evolves, without a significant increase in operational overhead.
[related-resource]
Learn more about Darktrace / OT
Darktrace / OT has a proven track record of detecting sophisticated threats at scale, get a deeper dive into the product here
.avif)





















.avif)