Nationally Targeted Cyber Attacks
As the digital world becomes more and more interconnected, the threat of cyber-attacks transcends borders and presents a significant concern to security teams worldwide. Yet despite this, some malicious actors have shown a tendency to focus their attacks on specific countries. By employing highly tailored tactics, techniques, and procedures (TTPs) to target users and organizations from one nation, rather than launching more widespread campaigns, threat actors are able to maximize the efficiency and efficacy of their attacks.
What is Guildma and how does it work?
One example can be seen in the remote access trojan (RAT) and information stealer, Guildma. Guildma, also known by the demonic moniker, Astaroth, first appeared in the wild in 2017 and is a Latin America-based banking trojan known to primarily target organizations in Brazil, although has more recently been observed in North America and Europe too [1].
By concentrating their efforts on Brazil, Guildma is able to launch attacks with a high degree of specificity, focussing their language on Brazilian norms, referencing Brazilian institutions, and tailoring their social engineering accordingly. Moreover, considering that Brazilian customers likely represent a relatively small portion of security vendors’ clientele, there may be a limited pool of available indicators of compromise (IoCs). This limitation could significantly impact the efficacy of traditional security measures that rely on signature-based detection methods in identifying emerging threats.
Darktrace vs. Guildma
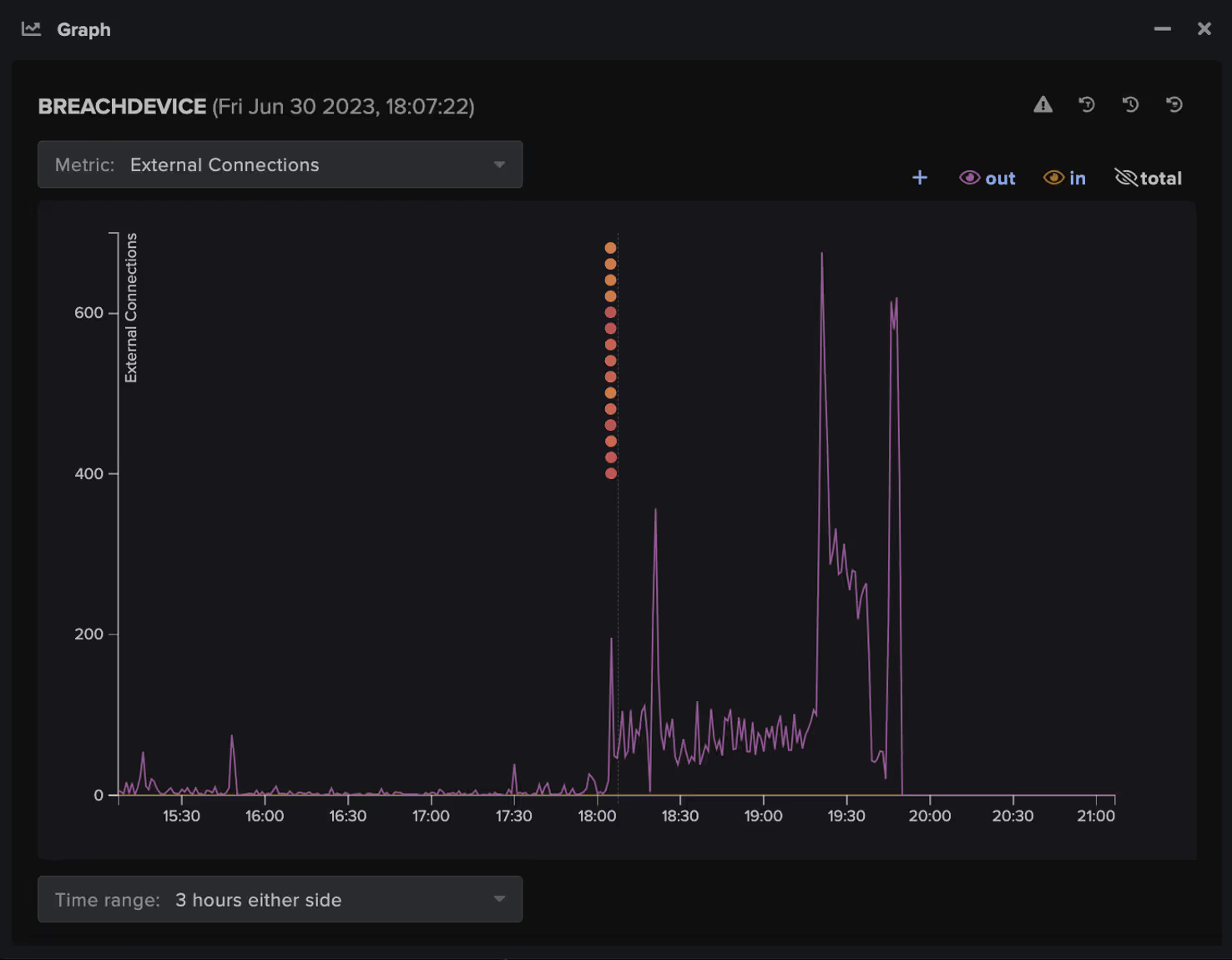
In June 2023, Darktrace observed a Guildma compromise on the network of a Brazilian customer in the manufacturing sector. The anomaly-based detection capabilities of Darktrace DETECT™ allowed it to identify suspicious activity surrounding the compromise, agnostic of any IoCs or specific signatures of a threat actor. Following the successful detection of the malware, the Darktrace Security Operations Center (SOC) carried out a thorough investigation into the compromise and brought it to the attention of the customer’s security team, allowing them to quickly react and prevent any further escalation.
This early detection by Darktrace effectively shut down Guildma operations on the network before any sensitive data could be gathered and stolen by malicious actors.
Attack Overview
In the case of the Guildma RAT detected by Darktrace, the affected system was a desktop device, ostensibly used by one employee. The desktop was first observed on the customer’s network in April 2023; however, it is possible that the initial compromise took place before Darktrace had visibility over the network. Guildma compromises typically start with phishing campaigns, indicating that the initial intrusion in this case likely occurred beyond the scope of Darktrace’s monitoring [2].
Early indicators
On June 23, 2023, Darktrace DETECT observed the first instance of unusual activity being performed by the affected desktop device, namely regular HTTP POST requests to a suspicious domain, indicative of command-and-control (C2) beaconing activity. The domain used an unusual Top-Level Domain (TLD), with a plausibly meaningful (in Portuguese) second-level domain and a seemingly random 11-character third-level domain, “dn00x1o0f0h.puxaofolesanfoneiro[.]quest”.
Throughout the course of this attack, Darktrace observed additional connections like this, representing something of a signature of the attack. The suspicious domains were typically registered within six months of observation, featured an uncommon TLD, and included a seemingly randomized third-level domain of 6-11 characters, followed by a plausibly legitimate second-level domain with a minimum of 15 characters. The connections to these unusual endpoints all followed a similar two-hour beaconing period, suggesting that Guildma may rotate its C2 infrastructure, using the Multi-Stage Channels TTP (MITRE ID T1104) to evade restrictions by firewalls or other signature-based security tools that rely on static lists of IoCs and “known bads”.

Living-off-the-land with BITS abuse
A week later, on June 30, 2023, the affected device was observed making an unusual Microsoft BITS connection. BitsAdmin is a deprecated administrative tool available on most Windows devices and can be leveraged by attackers to transfer malicious obfuscated payloads into and around an organization’s network. The domain observed during this connection, "cwiufv.pratkabelhaemelentmarta[.]shop”, follows the previously outlined domain naming convention. Multiple open-source intelligence (OSINT) sources indicated that the endpoint had links to malware and, when visited, redirected users to the Brazilian versions of WhatsApp and Zoom. This is likely a tactic employed by threat actors to ensure users are unaware of suspicious domains, and subsequent malware downloads, by redirected them to a trusted source.

Obfuscated Tooling Downloads
Within one minute of the suspicious BITS activity, Darktrace detected the device downloading a suspicious file from the aforementioned endpoint, (cwiufv.pratkabelhaemelentmarta[.]shop). The file in question appeared to be a ZIP file with the 17-digit numeric name query, namely “?37627343830628786”, with the filename “zodzXLWwaV.zip”.
However, Darktrace DETECT recognized that the file extension did not match its true file type and identified that it was, in fact, an executable (.exe) file masquerading as a ZIP file. By masquerading files downloads, threat actors are able to make their malicious files seem legitimate and benign to security teams and traditional security tools, thereby evading detection. In this case, the suspicious file in question was indeed identified as malicious by multiple OSINT sources.
Following the initial download of this masqueraded file, Darktrace also detected subsequent downloads of additional executable files from the same endpoint. It is possible that these downloads represented Guildma actors attempting to download additional tooling, including the information-stealer widely known as Astaroth, in order to begin its data collection and exfiltration operations.
Darktrace SOC
The successful detection of the masqueraded file transfer triggered an Enhanced Monitoring model breach, a high-fidelity model designed to detect activity that is more likely indicative of an ongoing compromise.
This breach was immediately escalated to the Darktrace SOC for analysis by Darktrace’s team of expert analysts who were able to complete a thorough investigation and notify the customer’s security team of the compromise in just over half an hour. The investigation carried out by Darktrace’s analysts confirmed that the activity was, indeed, malicious, and provided the customer’s security team with details around the extent of the compromise, the specific IoCs, and risks this compromise posed to their digital environment. This information empowered the customer’s security team to promptly address the issue, having a significant portion of the investigative burden reduced and resolved by the round-the-clock Darktrace analyst team.
In addition to this, Cyber AI Analyst™ launched an investigation into the ongoing compromise and was able to connect the anomalous HTTP connections to the subsequent suspicious file downloads, viewing them as one incident rather than two isolated events. AI Analyst completed its investigation in just three minutes, upon which it provided a detailed summary of events of the activity, further aiding the customer’s remediation process.

Conclusion
While the combination of TTPs observed in this Guildma RAT compromise is not uncommon globally, the specificity to targeting organizations in Brazil allows it to be incredibly effective. By focussing on just one country, malicious actors are able to launch highly specialized attacks, adapting the language used and tailoring the social engineering effectively to achieve maximum success. Moreover, as Brazil likely represents a smaller segment of security vendors’ customers, therefore leading to a limited pool of IoCs, attackers are often able to evade traditional signature-based detections.
Darktrace DETECT’s anomaly-based approach to threat detection allows for effective detection, mitigation, and response to emerging threats, regardless of the specifics of the attack and without relying on threat intelligence or previous IoCs. Ultimately in this case, Darktrace was able to identify the suspicious activity surrounding the Guildma compromise and swiftly bring it to the attention of the customer’s security team, before any data gathering, or exfiltration activity took place.
Darktrace’s threat detection capabilities coupled with its expert analyst team and round-the-clock SOC response is a highly effective addition to an organization’s defense-in-depth, whether in Brazil or anywhere else around the world.
Credit to Roberto Romeu, Senior SOC Analyst, Taylor Breland, Analyst Team Lead, San Francisco
References
https://malpedia.caad.fkie.fraunhofer.de/details/win.astaroth
https://www.welivesecurity.com/2020/03/05/guildma-devil-drives-electric/
Appendices
Darktrace DETECT Model Breaches
- Compromise / Agent Beacon (Long Period)
- Device / Unusual BITS Activity
- Anomalous File / Anomalous Octet Stream (No User Agent)
- Anomalous File / Masqueraded File Transfer (Enhanced Monitoring Model)
- Anomalous File / EXE from Rare External Location
- Anomalous File / Multiple EXE from Rare External Locations
List of IoCs
IoC Type - Description + Confidence
5q710e1srxk.broilhasoruikaliventiladorrta[.]shop - Domain - Likely C2 server
m2pkdlse8md.roilhasohlcortinartai[.]hair - Domain - Likely C2 server
cwiufv.pratkabelhaemelentmarta[.]shop - Domain - C2 server
482w5pct234.jaroilcasacorkalilc[.]ru[.]com - Domain - C2 server
dn00x1o0f0h.puxaofolesanfoneiro[.]quest - Domain - Likely C2 server
10v7mybga55.futurefrontier[.]cyou - Domain - Likely C2 server
f788gbgdclp.growthgenerator[.]cyou - Domain - Likely C2 server
6nieek.satqabelhaeiloumelsmarta[.]shop - Domain - Likely C2 server
zodzXLWwaV.zip (SHA1 Hash: 2a4062e10a5de813f5688221dbeb3f3ff33eb417 ) - File hash - Malware
IZJQCAOXQb.zip (SHA1 Hash: eaec1754a69c50eac99e774b07ef156a1ca6de06 ) - File hash - Likely malware
MITRE ATT&CK Mapping
ATT&CK Technique - Technique ID
Multi-Stage Channels - T1104
BITS Jobs - T1197
Application Layer Protocol: Web Protocols - T1071.001
Acquire Infrastructure: Web Services - T1583.006
Obtain Capabilities: Malware - T1588.001
Masquerading - T1036







































