At a Glance:
- Air gaps reduce cyber risk, but they do not prevent modern cyber attacks
- Having visibility into an air-gapped network is better than assuming your defenses are impenetrable and having zero visibility
- Darktrace can provide visibility and resiliency without jeopardizing the integrity of the air gap
What is an 'Air Gap'?
Information technology (IT) needs to fluidly connect with the outside world in order channel a flow of digital information across everything from endpoints and email systems to cloud and hybrid infrastructures. At the same time, this high level of connectivity makes IT systems particularly vulnerable to cyber-attacks.
Operational technology (OT), which controls the operations of physical processes, are considerably more sensitive. OT often relies on a high degree of regularity to maintain continuity of operations. Even the slightest disturbance can lead to disastrous results. Just a few seconds of delay on a programmable logic controller (PLC), for example, can significantly disrupt a manufacturing assembly line, leading to downtime at a considerable cost. In worst-case scenarios, disruptions to OT can even threaten human safety.
An air gap is a ‘digital moat’ where data cannot enter or leave OT environments unless it is transferred manually.
Organizations with OT have traditionally tried to reconcile this conflict between IT and OT by attempting to separate them completely. Essentially, the idea is to let IT do what IT does best — facilitate activities like communication and data transfer at rapid speeds, thus allowing people to connect with each other and access information and applications in an efficient capacity. But at the same time, erect an air gap between IT and OT so that any cyber threats that slip into IT systems do not then spread laterally into highly sensitive, mission-critical OT systems. This air gap is essentially a ‘digital moat’ where data cannot enter or leave OT environments unless it is transferred manually.
Limitations of the Air Gap
The air gap approach makes sense, but it is far from perfect. First, many organizations that believe they have completely air-gapped systems in fact have unknown points of IT/OT convergence, that is, connections between IT and OT networks of which they are unaware.
Many organizations today are also intentionally embracing IT/OT convergence to reap the benefits of digital transformation of their OT, in what is often called Industry 4.0. Examples include the industrial cloud (or ICSaaS), the industrial internet of things (IIoT), and other types of cyber-physical systems that offer increased efficiency and expanded capabilities when compared to more traditional forms of OT. Organizations may also embrace IT/OT convergence due to a lack of human capital, as convergence can make processes simpler and more efficient.
Even when an organization does have a true air gap (which is nearly impossible to confirm without full visibility across IT and OT environments), the fact is that there are a variety of ways for attackers to ‘jump the air gap'. Full visibility across IT and OT ecosystems in a single pane of glass is thus essential for organizations seeking to secure their OT. This is not only to illuminate any points of IT/OT convergence and validate the fact that an air gap exists in the first place, but also to see when an attack slips through the air gap.
.avif)
Air Gap Attack Vectors
Even a perfect air gap will be vulnerable to a variety of different attack vectors, including (but not limited to) the following:
- Physical compromise: An adversary bypasses physical security and gains access directly to the air-gapped network devices. Physical access is by far the most effective and obvious technique.
- Insider threats: Someone who is part of an organization and has access to air-gapped secure systems intentionally or unintentionally compromises a system.
- Supply chain compromise: A vendor with legitimate access to air-gapped systems unwittingly is compromised and brings infected devices into a network.
- Misconfiguration: Misconfiguration of access controls or permissions allows an attacker to access the air-gapped system through a separate device on the network.
- Social engineering (media drop): If an attacker was able to successfully conduct a malicious USB/media drop and an employee was to use that media within the air-gapped system, the network could be compromised.
- Other advanced tactics: Thermal manipulation, covert surface vibrations, LEDs, ultrasonic transmissions, radio signals, and magnetic fields are among a range of advanced tactics documented and demonstrated by researchers at Ben Gurion University.
Vulnerabilities of Air-Gapped Systems
Aside from susceptibility to advanced techniques, tactics, and procedures (TTPs) such as thermal manipulation and magnetic fields, more common vulnerabilities associated with air-gapped environments include factors such as unpatched systems going unnoticed, lack of visibility into network traffic, potentially malicious devices coming on the network undetected, and removable media being physically connected within the network.
Once the attack is inside OT systems, the consequences can be disastrous regardless of whether there is an air gap or not. However, it is worth considering how the existence of the air gap can affect the time-to-triage and remediation in the case of an incident. For example, the existence of an air gap may seriously limit an incident response vendor’s ability to access the network for digital forensics and response.
Kremlin Hackers Jumping the Air Gap
In 2018, the U.S. Department of Homeland Security (DHS) issued an alert documenting the TTPs used by Russian threat actors known as Dragonfly and Energetic Bear. Further reporting alleged that these groups ‘jumped the air gap,’ and, concerningly, gained the ability to disable the grid at the time of their choosing.
These attackers successfully gained access to sensitive air-gapped systems across the energy sector and other critical infrastructure sectors by targeting vendors and suppliers through spear-phishing emails and watering hole attacks. These vendors had legitimate access to air-gapped systems, and essentially brought the infection into these systems unintentionally when providing support services such as patch deployment.
This incident reveals that even if a sensitive OT system has complete digital isolation, this robust air gap still cannot fully eliminate one of the greatest vulnerabilities of any system—human error. Human error would still hold if an organization went to the extreme of building a faraday cage to eliminate electromagnetic radiation. Air-gapped systems are still vulnerable to social engineering, which exploits human vulnerabilities, as seen in the tactics that Dragonfly and Energetic Bear used to trick suppliers, who then walked the infection right through the front door.
Ideally, a technology would be able to identify an attack regardless of whether it is caused by a compromised supplier, radio signal, or electromagnetic emission. By spotting subtle deviations from a device, human, or network’s normal ‘pattern of life’, Self-Learning AI detects even the most nuanced forms of threatening behavior as they emerge — regardless of the source or cause of the threat.
Darktrace/OT for Air-Gapped Environments
Darktrace/OT for air-gapped environments is a physical appliance that deploys directly to the air-gapped system. Using raw digital data from an OT network to understand the normal pattern of life, Darktrace/OT does not need any data or threat feeds from external sources because the AI builds an innate understanding of self without third-party support.
Because all data-processing and analytics are performed locally on the Darktrace appliance, there is no requirement for Darktrace to have a connection out to the internet. As a result, Darktrace/OT provides visibility and threat detection to air-gapped or highly segmented networks without jeopardizing their integrity. If a human or machine displays even the most nuanced forms of threatening behavior, the solution can illuminate this in real time.
Security professionals can then securely access Darktrace alerts from anywhere within the network, using a web browser and encrypted HTTPS, and in line with your organization’s network policies.
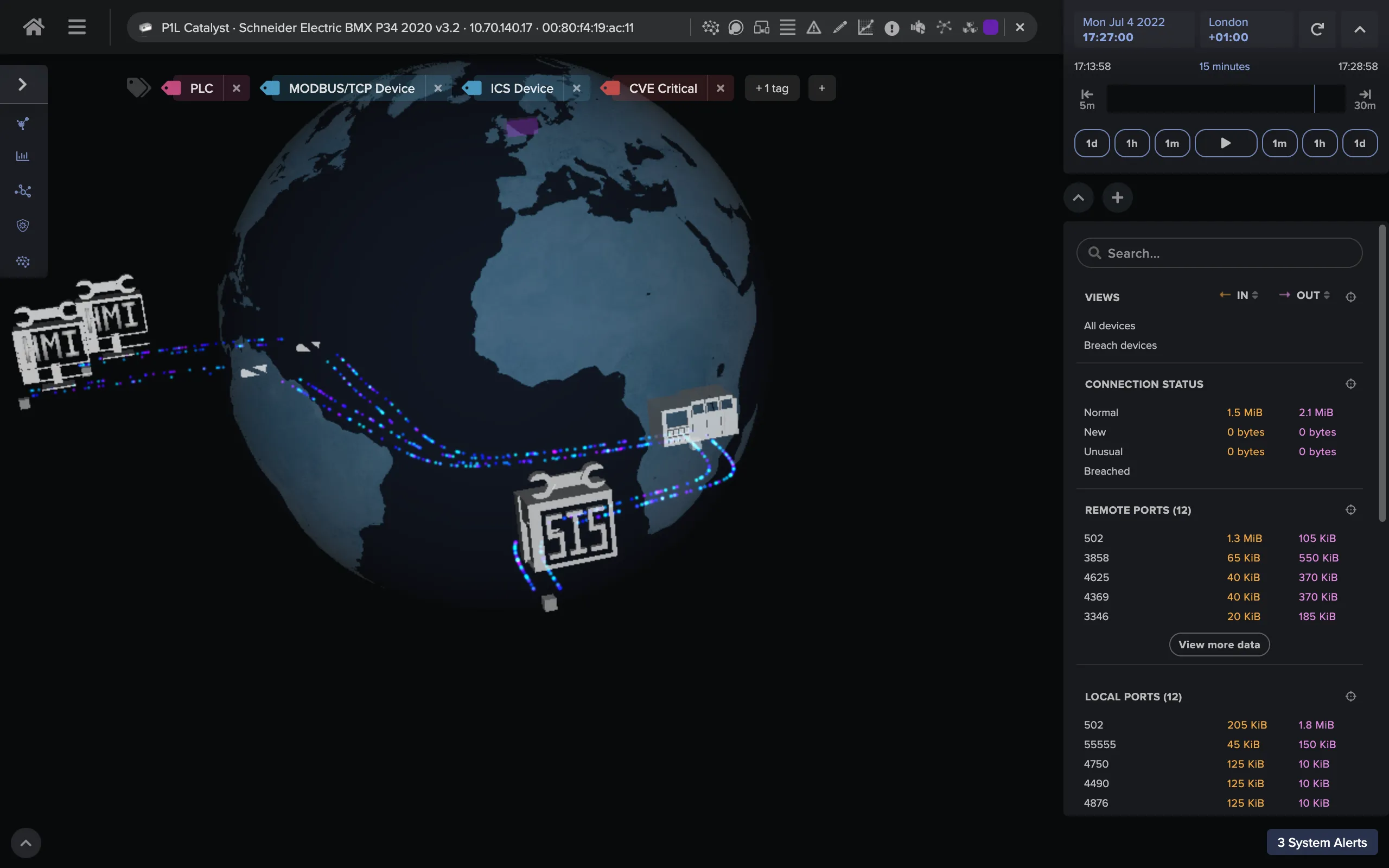
With this deployment, Darktrace offers all the critical insights demonstrated in other Darktrace/OT deployments, including (but not limited to) the following:
- Illuminating all points of IT/OT convergence, including unknown points of IT/OT convergence in ‘air gapped’ environments
- OT network visibility across all Purdue Levels to the field controller level
- OT asset inventory
- CVE tracking
- Identification of new devices on the network, first seen devices, and last seen active devices
- Threat response and incident reporting that the IT team, security professionals, operators, and engineering can easily read
Organizations seeking to validate whether they have an air gap in the first place and maintain the air gap as their IT and OT environments evolve will greatly benefit from the comprehensive visibility and continuous situational awareness offered by Darktrace’s Self-Learning AI. Also, organizations looking to poke holes in their air gap to embrace the benefits of IT/OT convergence will find that Self-Learning AI’s vigilance spots cyber-attacks that slip through.
Whatever your organizations goals—be it embracing IIoT or creating a full-blown DMZ—by learning ‘you’, Darktrace’s Self-Learning AI can help you achieve them safely and securely.
Credit to: Daniel Simonds and Oakley Cox for their contribution to this blog.