Part 1: How to Achieve Proactive Network Security
Part 2: Overcoming Alert Fatigue with AI-Led Investigations
While the success of a SOC team is often measured through incident management effectiveness (E.g MTTD, MTTR), a true measure of maturity is the reduction of annual security incidents.
Organizations face an increasing number of alerts each year, yet the best SOC teams place focus on proactive operations which don’t reduce the threshold for what becomes an incident but targets the source risks that prevent them entirely.
Freeing up time to focus on cyber risk management is a challenge in and of itself, we cover this in the previous two blogs in this series (see above). However, when the time comes to manage risk, there are several challenges that are unique when compared to detection & response functions within cybersecurity.
Why do cyber risks matter?
While the volume of reported CVEs is increasing at an alarming rate[1], determining the criticality of each vulnerability is becoming increasingly challenging, especially when the likelihood and impact may be different for each organization. Yet vulnerabilities have stood as an important signpost in traditional security and mitigation strategies. Now, without clear prioritization, potentially severe risks may go unreported, leaving organizations exposed to significant threats.
Vulnerabilities also represent just one area of potential risks. Cyberattacks are no longer confined to a single technology type. They now traverse various platforms, including cloud services, email systems, and networks. As technology infrastructure continues to expand, so does the attack surface, making comprehensive visibility across all technology types essential for reducing risk and preventing multi-vector attacks.
However, achieving this visibility is increasingly difficult as infrastructure grows and the cyber risk market remains oversaturated. This visibility challenge extends beyond technology to include personnel and individual cyber hygiene which can still exacerbate broader cyberattacks whether malicious or not.
Organizations must adopt a holistic approach to preventative security. This includes improving visibility across all technology types, addressing human risks, and mobilizing swiftly against emerging security gaps.
“By 2026, 60% of cybersecurity functions will implement business-impact-focused risk assessment methods, aligning cybersecurity strategies with organizational objectives.” [2]
The costs of a fragmented approach

Unlike other security tools (like SIEM, NDR or SOAR) which contain an established set of capabilities, cyber risk reduction has not traditionally been defined by a single market, rather a variety of products and practices that each provide their own value and are overwhelming if too many are adopted. Just some examples include:
- Threat and Vulnerability management: Leverages threat intelligence, CVEs and asset management; however, leaves teams with significant patching workflows, ignores business & human factors and is reliant on the speed of teams to keep up with each passing update.
- Continuous Controls Monitoring (CCM): Automatically audits the effectiveness of security controls based on industry frameworks but requires careful prioritization and human calculations to set-up effectively. Focuses solely on mobilization.
- Breach and Attack Simulation (BAS): Automates security posture testing through mock scenarios but require previous prioritization and might not tell you how your specific technologies can be mitigated to reduce that risk.
- Posture Management technologies: Siloed approaches across Cloud, SaaS, Data Security and even Gen AI that reactively assess misconfigurations and suggest improvements but with only industry frameworks to validate the importance of the risks.
- Red teaming & Penetration testing: Required by several regulations including (GDPR, HIPPA, PCI, DSS), many organizations hire 'red teams' to perform real breaches in trusted conditions. Penetration tests reveal many flaws, but are not continuous, requiring third-party input and producing long to-do lists with input of broader business risk dependent on the cost of the service.
- Third-party auditors: Organizations also use third-party auditors to identify assets with vulnerabilities, grade compliance, and recommend improvements. At best, these exercises become tick-box exercises for companies to stay in compliance with the responsibility still on the client to perform further discovery and actioning.
Many of these individual solutions on the market offer simple enhancement, or an automated version of an existing human security task. Ultimately, they lack an understanding of the most critical assets at your organization and are limited in scope, only working in a specific technology area or with the data you provide.
Even when these strategies are complete, implementation of the results require resources, coordination, and buy-in from IT, cybersecurity, and compliance departments. Given the nature of modern business structures, this can be labor and time intensive as responsibilities are shared by organizational segmentation spread across IT, governance, risk and compliance (GRC), and security teams.
Prioritize your true cyber risk with a CTEM approach
Organizations with robust security programs benefit from well-defined policies, standards, key risk indicators (KRIs), and operational metrics, making it easier to measure and report cyber risk accurately.
Implementing a framework like Gartner’s CTEM (Continuous Threat Exposure Management) can help governance by defining the most relevant risks to each organization and which specific solutions meet your improvement needs.
This five-step approach—scoping, discovery, prioritization, validation, and mobilization—encourages focused management cycles, better delegation of responsibilities and a firm emphasis on validating potential risks through technological methods like attack path modeling or breach and attack simulation to add credibility.
Implementing CTEM requires expertise and structure. This begins with an exposure management solution developed uniquely alongside a core threat detection and response offering, to provide visibility of an organization’s most critical risks, whilst linking directly to their incident-based workflows.
“By 2026, organizations prioritizing their security investments, based on a continuous threat exposure management program, will realize a two-third reduction in breaches.” [3]
Achieving a proactive security posture across the whole estate
Unlike conventional tools that focus on isolated risks, Darktrace / Proactive Exposure Management breaks down traditional barriers. Teams can define risk scopes with full, prioritized visibility of the critical risks between: IT/OT networks, email, Active Directory, cloud resources, operational groups, (or even the external attack surface by integrating with Darktrace / Attack Surface Management).
Our innovative, AI-led risk discovery provides a view that mirrors actual attacker methodologies. It does this through advanced algorithms that determine risk based on business importance, rather than traditional device-type prioritization. By implementing a sophisticated damage assessment methodology, security teams don’t just prioritize via severity but instead, the inherent impact, damage, weakness and external exposure of an asset or user.
These calculations also revolutionize vulnerability management by combining industry standard CVE measurements with that organization-specific context to ensure patch management efforts are efficient, rather than an endless list.
Darktrace also integrates MITRE ATT&CK framework mappings to connect all risks through attack path modeling. This offers validation to our AI’s scoring by presenting real world incident scenarios that could occur across your technologies, and the actionable mitigations to mobilize against them.
For those human choke points, security may also deploy targeted phishing engagements. These send real but harmless email ‘attacks’ to test employee susceptibility, strengthening your ability to identify weak points in your security posture, while informing broader governance strategies.
Combining risk with live detection and response
Together, each of these capabilities let teams take the best steps towards reducing risk and the volume of incidents they face. However, getting proactive also sharpens your ability to handle live threats if they occur.
During real incidents Darktrace users can quickly evaluate the potential impact of affected assets, create their own risk detections based on internal policies, strengthen their autonomous response along critical attack paths, or even see the possible stage of the next attack.
By continually ingesting risk information into live triage workflows, security teams will develop a proactive-first mindset, prioritizing the assets and alerts that have the most impact to the business. This lets them utilize their resource in the most efficient way, freeing up even more time for risk management, mitigation and ensuring continuity for the business.
Whether your organization is laying the foundation for a cybersecurity program or enhancing an advanced one, Darktrace’s self-learning AI adapts to your needs:
- Foundational stage: For organizations establishing visibility and automating detection and response.
- Integrated stage: For teams expanding coverage across domains and consolidating tools for simplicity.
- Proactive stage: For mature security programs enhancing posture with vulnerability management and risk prioritization.
The Darktrace ActiveAI Security Platform empowers security teams to adopt a preventative defense strategy by using Cyber AI Analyst and autonomous response to fuel quicker triage, incident handling and give time back for proactive efforts designed around business impact. The platform encapsulates the critical capabilities that help organizations be proactive and stay ahead of evolving threats.

Download the solution brief
Maximize security visibility and reduce risk:
- Unify risk exposure across all technologies with AI-driven scoring for CVEs, human communications, and architectures.
- Gain cost and ROI insights on CVE risks, breach costs, patch latency, and blind spots.
- Strengthen employee awareness with targeted phishing simulations and training.
- Align proactive and reactive security by assessing device compromises and prevention strategies.
- Reduce risk with tailored guidance that delivers maximum impact with minimal effort.
Take control of your security posture today. Download here!
References
[1] https://nvd.nist.gov/vuln/search, Search all, Statistics, Total matches By Year 2023 against 2024
[2] https://www.gartner.com/en/documents/5598859
[3] https://www.gartner.com/en/articles/how-to-manage-cybersecurity-threats-not-episodes





































![Geographical distribution of organization’s affected by Akira ransomware in 2025 [9].](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/68e684a90c107be86fa5c2e0_Screenshot%202025-10-08%20at%207.53.20%E2%80%AFAM.png)
![Flowchart of Kerberos PKINIT pre-authentication and U2U authentication [12].](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/68e53a2b5e9394d5a5cbebb7_Screenshot%202025-10-07%20at%209.04.43%E2%80%AFAM.png)

![Cyber AI Analyst investigation into the suspicious file download and suspected C2 activity between the ESXI device and the external endpoint 137.184.243[.]69.](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/68e53a8ea01e348d5a62a6c3_Screenshot%202025-10-07%20at%209.06.31%E2%80%AFAM.png)
![Packet capture (PCAP) of connections between the ESXi device and 137.184.243[.]69.](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/68e53ae5304f84a4192967db_Screenshot%202025-10-07%20at%209.07.53%E2%80%AFAM.png)
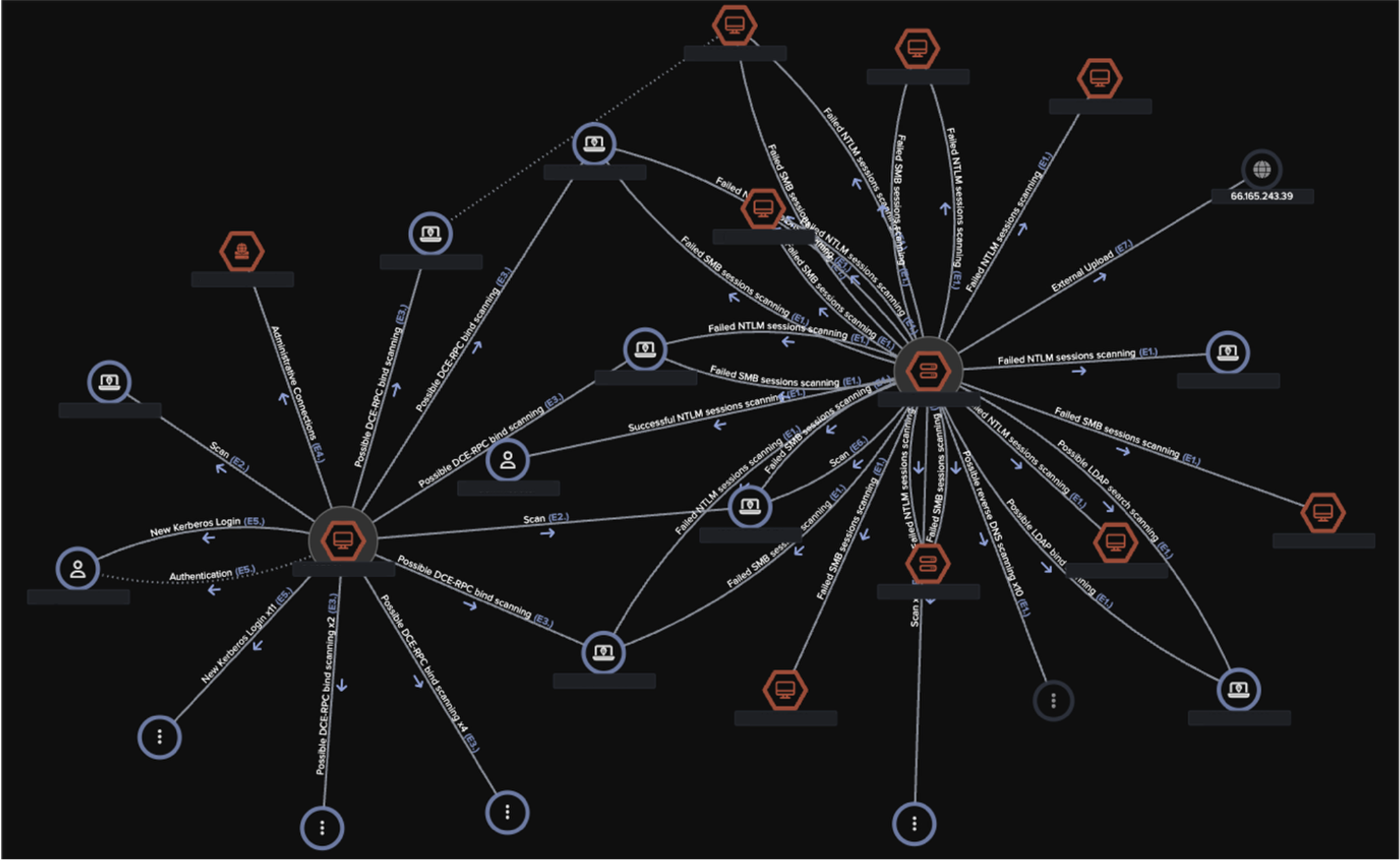
![Cyber AI Analyst incident view highlighting multiple unusual events across several devices on August 20. Notably, it includes the “Unusual External Data Transfer” event, which corresponds to the anomalous 2 GB data upload to the known Akira-associated endpoint 66.165.243[.]39.](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/68e53b26d90343a0a6ab3bb2_Screenshot%202025-10-07%20at%209.09.02%E2%80%AFAM.png)