From credit card details and medical records, through to private conversations and even dating preferences, the modern consumer entrusts an unprecedented number of organizations with their most sensitive information, hoping against hope that it will be stored on the digital equivalent of Fort Knox.
The reality, however, is that robust data privacy has thus far proven elusive. Almost 13 billion records were breached over the last two years — including from Facebook, Google, and the US Postal Service — demonstrating once again that no network perimeter can keep motivated attackers at bay.
For governments whose principal responsibility is to safeguard their citizens, implementing a strong data protection regime is therefore as challenging as it is critical. At a time when cyber-criminals find vulnerabilities in the most ostensibly airtight systems, these regulators have tended to shy away from mandating concrete security practices, since no one can anticipate which measures will repel the next unpredictable attack. Instead, most data protection laws default to ambiguous calls for “reasonable,” “adequate,” or “appropriate” cyber defenses — language that arguably renders any breached company noncompliant by definition.
While such ambiguity makes prediction pieces like this one speculative to some extent, the coming year will almost certainly witness both an increase in data protection laws around the world as well as a less forgiving interpretation of their requirements. Ultimately, as governments attempt to address growing public concern over data privacy, the mere fact of having suffered a breach could be seen as grounds for significant fines. Avoiding these fines — and doing right by one’s customers — entails assuming that the bad guys will inevitably get past the perimeter.

Figure 1: Noncompliance penalties are only getting larger as the 2020s near. Data source: CSO.
GDPR goes global
The EU’s adoption of the General Data Protection Regulation (GDPR) in April 2016 was the watershed moment in the history of data protection legislation. Its enumeration of individual privacy rights, its 72-hour breach notification requirement, and its broad data protection directives continue to serve as a blueprint for countless others, such as Brazil’s General Data Protection Law (LGPD), Thailand’s Personal Data Protection Act (PDPA), and the California Consumer Privacy Act (CCPA). All three of these regulations become enforceable in 2020, with major ramifications for companies worldwide.
Brazil’s law, which will go into effect on August 15, 2020, is modeled closely after GDPR. Like GDPR, the law applies to all companies that handle the personal data of any of Brazil’s 210 million residents — regardless of where these companies themselves are headquartered. Also like GDPR, of course, the LGPD’s security clauses are open to interpretation. The law compels data handlers to “adopt security, technical, and administrative measures able to protect personal data from unauthorized access,” taking into account “the current state of technology.”
The PDPA in Thailand — effective starting on May 27, 2020 — is similarly vague in mandating unspecified security measures. It parts company, however, in that violators face the possibility of criminal prosecution and even imprisonment for up to one year, in addition to civil damages. Organizations classified as Critical Information Infrastructure (CII), including banks, telecoms, utilities, and hospitals, are regulated under Thailand’s separate Cybersecurity Act and its slightly more detailed obligations.

Figure 2: New GDPR-inspired laws like Brazil’s will turn this map increasingly blue. Image source: DLA Piper.
In California, meanwhile, the CCPA will enforce noncompliance penalties of up to $750 per consumer per incident beginning on the first day of 2020, which could result in multibillion-dollar fines in the case of large-scale breaches. Such precise provisions indicate that GDPR-style legislation is more than a symbolic step toward data protection. And yet, as of August 2019, only 2% of companies reported that they were fully compliant with CCPA, perhaps because, according to a state-commissioned study, California firms will be forced to shell out $55 billion on just their initial compliance efforts.
Checkmate for checkbox compliance
Between the hundreds of data protection fines levied under GDPR and analogous laws, the common thread is that penalized companies are deemed to have suffered a preventable breach. For instance, in the aftermath of the 2017 Equifax compromise that exposed the personal information of more than 140 million consumers, the company was found to have been in violation of the FTC Safeguards Rule, which compelled it to adopt security measures “appropriate to [the] size and complexity” of its digital infrastructure. The US government concluded that the incident was “entirely preventable” had Equifax performed a “routine” security update on the impacted database — an oversight that precipitated at least $1.4 billion in total damages.
However, a closer inspection reveals challenges far deeper than just a simple oversight. Equifax did indeed scan its network for vulnerabilities, but the automated scanner it used was not properly configured to search all of its assets. The truth is that these kinds of misconfigurations and blind spots are a symptom of the conventional approach to cyber security itself, an approach reliant on humans to adjust and monitor a vast array of siloed security tools. In the context of cloud environments designed to be dynamic and IoT devices that are often unbeknownst to the security team, there is nothing routine about defending the “size and complexity” of the modern enterprise.
The upshot of all these new laws, requirements, and fines is that the days of mere checkbox compliance are over. Breached companies can no longer throw up their hands and point to the list of perimeter security tools they had in place, particularly because attackers largely exploit user errors and misconfigurations that — while inevitable — also appear preventable in a vacuum. Rather, to achieve compliance in 2020, human teams need artificial intelligence to make sense of their dynamic digital estates. By learning how each unique user and device normally functions while ‘on the job’, such Cyber AI detects threats that are already inside the perimeter — before they cost the company in court.




















![PCAP highlighting the HTTP GET request that sends information to the specific IP, 193.36.38[.]237, which then generates another numeric file titled per the current time.](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/684068fac1b4368f672c17cc_Screenshot%202025-06-04%20at%208.40.32%E2%80%AFAM.png)
![PCAP highlighting HTTP POST connection with the numeric file per the URI /1744205200 that indicates data exfiltration to 193.36.38[.]237.](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/6840694509d92b6220ccf5f1_Screenshot%202025-06-04%20at%208.41.48%E2%80%AFAM.png)


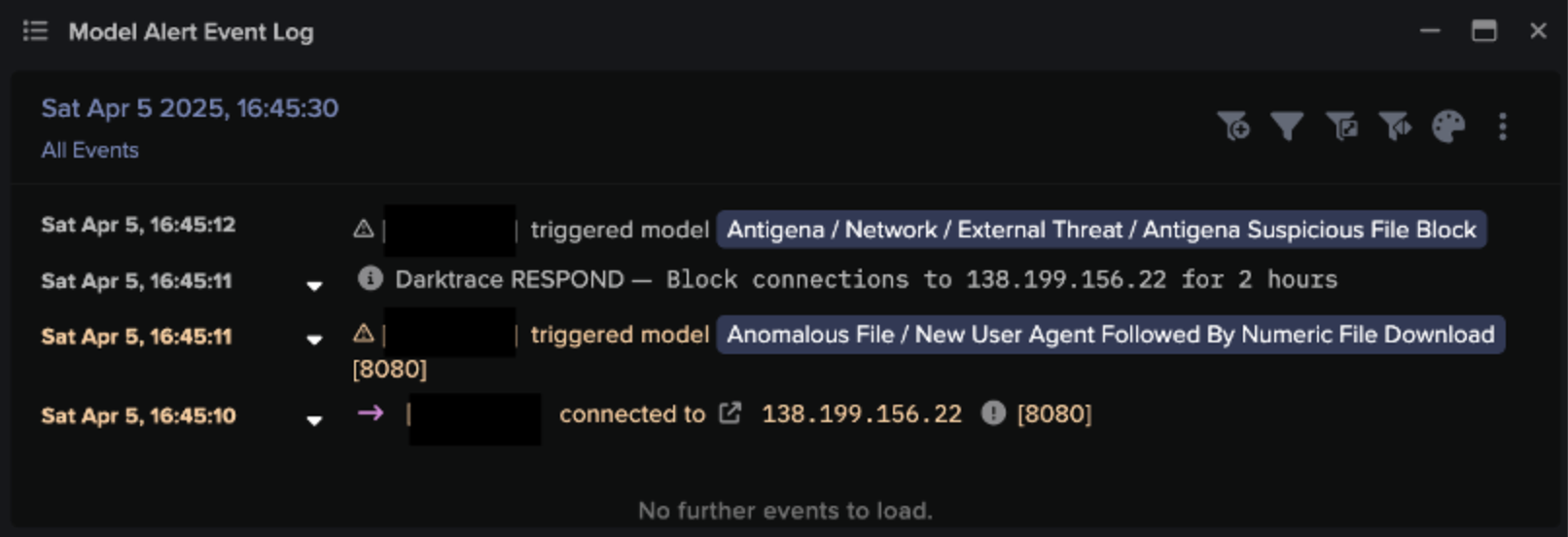
![Autonomous Response blocked connections to malicious endpoints, including 138.199.156[.]22, 185.250.151[.]155, and rkuagqnmnypetvf[.]top, and also quarantined the affected device. These actions were later manually reinforced by the Darktrace SOC.](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/68406a1f723c9d6fda9c5268_Screenshot%202025-06-04%20at%208.45.23%E2%80%AFAM.png)
