We are thrilled to announce that Darktrace has been named the only Visionary in the inaugural Gartner® Magic Quadrant™ for Cyber-Physical Systems (CPS) Protection Platforms. We feel This recognition highlights Darktrace’s AI-driven approach to securing industrial environments, where conventional security solutions struggle to keep pace with increasing cyber threats.
A milestone for CPS security
It's our opinion that the first-ever Gartner Magic Quadrant for CPS Protection Platforms reflects a growing industry shift toward purpose-built security solutions for critical infrastructure. As organizations integrate IT, OT, and cloud-connected systems, the cyber risk landscape continues to expand. Gartner evaluated 17 vendors based on their Ability to Execute and Completeness of Vision, establishing a benchmark for security leaders looking to enhance cyber resilience in industrial environments.
We believe the Gartner recognition of Darktrace as the only Visionary reaffirms the platform’s ability to proactively defend against cyber risks through AI-driven anomaly detection, autonomous response, and risk-based security strategies. With increasingly sophisticated attacks targeting industrial control systems, organizations need a solution that continuously evolves to defend against both known and unknown threats.
AI-driven security for CPS environments
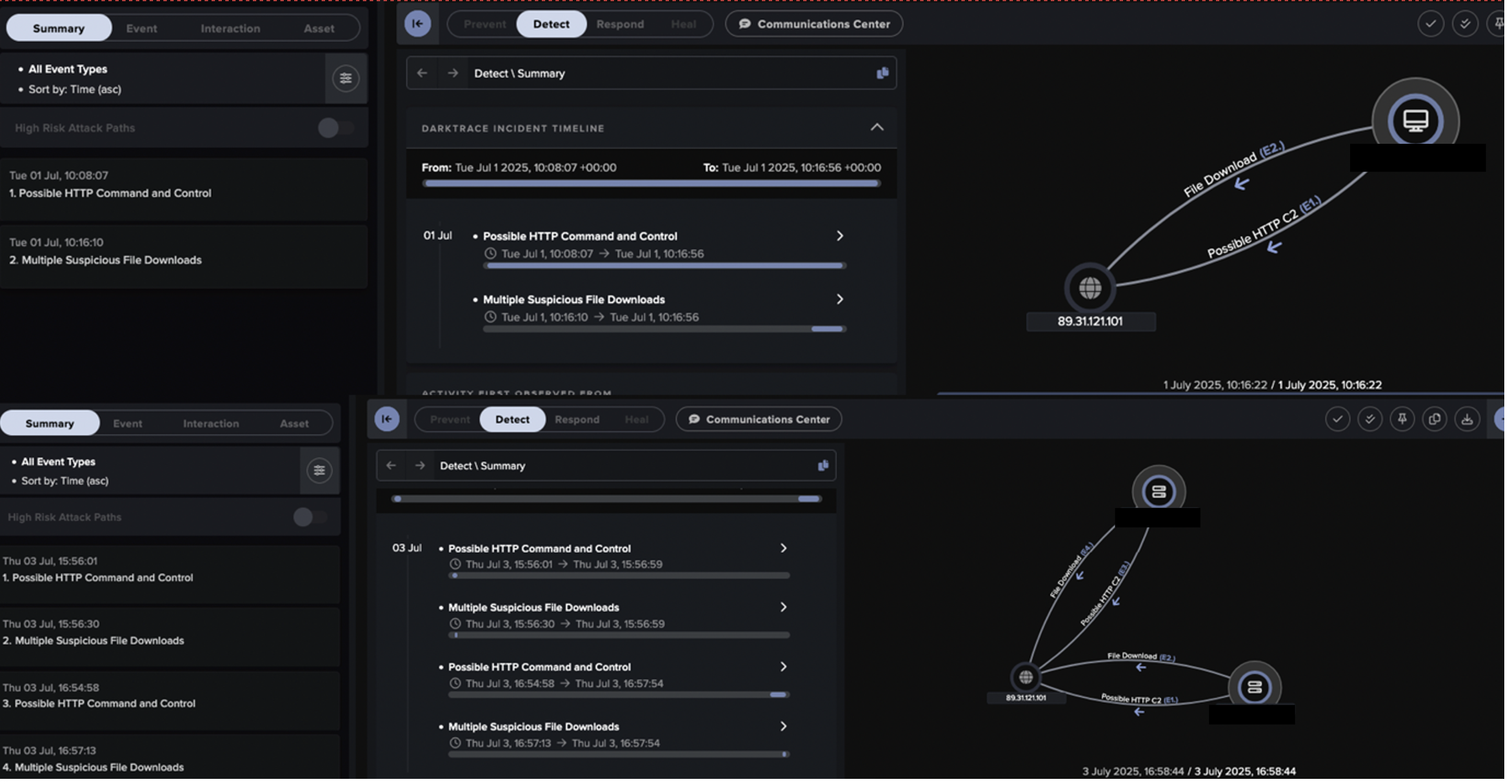
Securing CPS environments requires an approach that adapts to the dynamic nature of industrial operations. Traditional security tools rely on static signatures and predefined rules, leaving gaps in protection against novel and sophisticated threats. Darktrace / OT takes a different approach, leveraging Self-Learning AI to detect and neutralize threats in real time, even in air-gapped or highly regulated environments.
Darktrace / OT continuously analyzes network behaviors to establish a deep understanding of what is “normal” for each industrial environment. This enables it to autonomously identify deviations that signal potential cyber threats, providing early warning and proactive defense before attacks can disrupt operations. Unlike rule-based security models that require constant manual updates, Darktrace / OT improves with the environment, ensuring long-term resilience against emerging cyber risks.
Bridging the IT-OT security gap
A major challenge for organizations protecting CPS environments is the disconnect between IT and OT security. While IT security has traditionally focused on data
protection and compliance, OT security is driven by operational uptime and safety, leading to siloed security programs that leave critical gaps in visibility and response.
Darktrace / OT eliminates these silos by providing unified visibility across IT, OT, and IoT assets, ensuring that security teams have a complete picture of their attack surface. Its AI-driven approach enables cross-domain threat detection, recognizing risks that move laterally between IT and OT environments. By seamlessly integrating with existing security architectures, Darktrace / OT helps organizations close security gaps without disrupting industrial processes.
Proactive OT risk management and resilience
Beyond detection and response, Darktrace / OT strengthens organizations’ ability to manage cyber risk proactively. By mapping vulnerabilities to real-world attack paths, it prioritizes remediation actions based on actual exploitability and business impact, rather than relying on isolated CVE scores. This risk-based approach enables security teams to focus resources where they matter most, reducing overall exposure to cyber threats.
With autonomous threat response capabilities, Darktrace / OT not only identifies risks but also contains them in real time, preventing attackers from escalating intrusions. Whether mitigating ransomware, insider threats, or sophisticated nation-state attacks, Darktrace / OT ensures that industrial environments remain secure, operational, and resilient, no matter how threats evolve.
AI-powered incident response and SOC automation
Security teams are facing an overwhelming volume of alerts, making it difficult to prioritize threats and respond effectively. Darktrace / OT’s Cyber AI Analyst acts as a force multiplier for security teams by automating threat investigation, alert triage, and response actions. By mimicking the workflow of a human SOC analyst, Cyber AI Analyst provides contextual insights that accelerate incident response and reduce the manual workload on security teams.
With 24/7 autonomous monitoring, Darktrace / OT ensures that threats are continuously detected and investigated in real time. Whether facing ransomware, insider threats, or sophisticated nation-state attacks, organizations can rely on AI-driven security to contain threats before they disrupt operations.
Trusted by customers: Darktrace / OT recognized in Gartner Peer Insights

Beyond our recognition in the Gartner Magic Quadrant, we feel Darktrace / OT is one of the highest-rated CPS security solutions on Gartner Peer Insights, reflecting strong customer trust and validation. With a 4.9/5 overall rating and the highest "Willingness to Recommend" score among CPS vendors, organizations across critical infrastructure and industrial sectors recognize the impact of our AI-driven security approach. Source: Gartner Peer Insights (Oct 28th)
This strong customer endorsement underscores why leading enterprises trust Darktrace / OT to secure their CPS environments today and in the future.
Redefining the future of CPS security
It's our view that Darktrace’s recognition as the only Visionary in the Gartner Magic Quadrant for CPS Protection Platforms validates its leadership in next-generation industrial security. As cyber threats targeting critical infrastructure continue to rise, organizations must adopt AI-driven security solutions that can adapt, respond, and mitigate risks in real time.
We believe this recognition reinforces our commitment to innovation and our mission to secure the world’s most essential systems. This recognition reinforces our commitment to innovation and our mission to secure the world’s most essential systems.
® Request a demo to see Darktrace OT in action.
Gartner, Magic Quadrant for CPS Protection Platforms , Katell Thielemann, Wam Voster, Ruggero Contu 12 February 2025
Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
GARTNER is a registered trademark and service mark of Gartner and Magic Quadrant and Peer Insights are a registered trademark, of Gartner, Inc. and/or its affiliates in the U.S. and internationally and are used herein with permission. All rights reserved. Gartner Peer Insights content consists of the opinions of individual end users based on their own experiences with the vendors listed on the platform, should not be construed as statements of fact, nor do they represent the views of Gartner or its affiliates. Gartner does not endorse any vendor, product or service depicted in this content nor makes any warranties, expressed or implied, with respect to this content, about its accuracy or completeness, including any warranties of merchantability or fitness for a particular purpose.