Introduction
Across an ever changing cyber landscape, it is common place for threat actors to actively identify and exploit newly discovered vulnerabilities within commonly utilized services and applications. While attackers are likely to prioritize developing exploits for the more severe and global Common Vulnerabilities and Exposures (CVEs), they typically have the most success exploiting known vulnerabilities within the first couple years of disclosure to the public.
Addressing these vulnerabilities in a timely manner reduces the effectiveness of known vulnerabilities, decreasing the pace of malicious actor operations and forcing pursuit of more costly and time-consuming methods, such as zero-day related exploits or attacking software supply chain operations. While actors also develop tools to exploit other vulnerabilities, developing exploits for critical and publicly known vulnerabilities gives actors impactful tools at a low cost they are able to use for quite some time.
Between January and March 2024, the Darktrace Threat Research team investigated one such example that involved indicators of compromise (IoCs) suggesting the exploitation of vulnerabilities in ConnectWise’s remote monitoring and management (RMM) software ScreenConnect.
What are the ConnectWise ScreenConnect vulnerabilities?
CVE-2024-1708 is an authentication bypass vulnerability in ScreenConnect 23.9.7 (and all earlier versions) that, if exploited, would enable an attacker to execute remote code or directly impact confidential information or critical systems. This exploit would pave the way for a second ScreenConnect vulnerability, CVE-2024-1709, which allows attackers to directly access confidential information or critical systems [1].
ConnectWise released a patch and automatically updated cloud versions of ScreenConnect 23.9.9, while urging security teams to update on-premise versions immediately [3].
If exploited in conjunction, these vulnerabilities could allow a malicious actor to create new administrative accounts on publicly exposed instances by evading existing security measures. This, in turn, could enable attackers to assume an administrative role and disable security tools, create backdoors, and disrupt RMM processes. Access to an organization’s environment in this manner poses serious risk, potentially leading to significant consequences such as deploying ransomware, as seen in various incidents involving the exploitation of ScreenConnect [2]
Darktrace Coverage of ConnectWise Exploitation
Darktrace’s anomaly-based detection was able to identify evidence of exploitation related to CVE-2024-1708 and CVE-2024-1709 across two distinct timelines; these detections included connectivity with endpoints that were later confirmed to be malicious by multiple open-source intelligence (OSINT) vendors. The activity observed by Darktrace suggests that threat actors were actively exploiting these vulnerabilities across multiple customer environments.
In the cases observed across the Darktrace fleet, Darktrace DETECT™ and Darktrace RESPOND™ were able to work in tandem to pre-emptively identify and contain network compromises from the onset. While Darktrace RESPOND was enabled in most customer environments affected by the ScreenConnect vulnerabilities, in the majority of cases it was configured in Human Confirmation mode. Whilst in Human Confirmation mode, RESPOND will provide recommended actions to mitigate ongoing attacks, but these actions require manual approval from human security teams.
When enabled in autonomous response mode, Darktrace RESPOND will take action automatically, shutting down suspicious activity as soon as it is detected without the need for human intervention. This is the ideal end state for RESPOND as actions can be taken at machine speed, without any delays waiting for user approval.
Looking within the patterns of activity observed by Darktrace , the typical attack timeline included:
Darktrace observed devices on affected customer networks performing activity indicative of ConnectWise ScreenConnect usage, for example connections over 80 and 8041, connections to screenconnect[.]com, and the use of the user agent “LabTech Agent”. OSINT research suggests that this user agent is an older name for ConnectWise Automate [5] which also includes ScreenConnect as standard [6].
![Darktrace DETECT model alert highlighting the use of a remote management tool, namely “screenconnect[.]com”.](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/663e65c6b0ee97378e4509af_Screenshot%202024-05-10%20at%2011.21.43%20AM.avif)
This activity was typically followed by anomalous connections to the external IP address 108.61.210[.]72 using URIs of the form “/MyUserName_DEVICEHOSTNAME”, as well as additional connections to another external, IP 185.62.58[.]132. Both of these external locations have since been reported as potentially malicious [14], with 185.62.58[.]132 in particular linked to ScreenConnect post-exploitation activity [2].
![Figure 2: Darktrace DETECT model alert highlighting the unusual connection to 185.62.58[.]132 via port 8041.](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/663e66b4de1b5491cb1af256_Screenshot%202024-05-10%20at%2011.22.47%20AM.avif)
![Figure 3: Darktrace DETECT model alert highlighting connections to 108.61.210[.]72 using a new user agent and the “/MyUserName_DEVICEHOSTNAME” URI.](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/663e66d3c53f1631e9d6f3ec_Screenshot%202024-05-10%20at%2011.23.04%20AM.avif)
Same Exploit, Different Tactics?
While the majority of instances of ConnectWise ScreenConnect exploitation observed by Darktrace followed the above pattern of activity, Darktrace was able to identify some deviations from this.
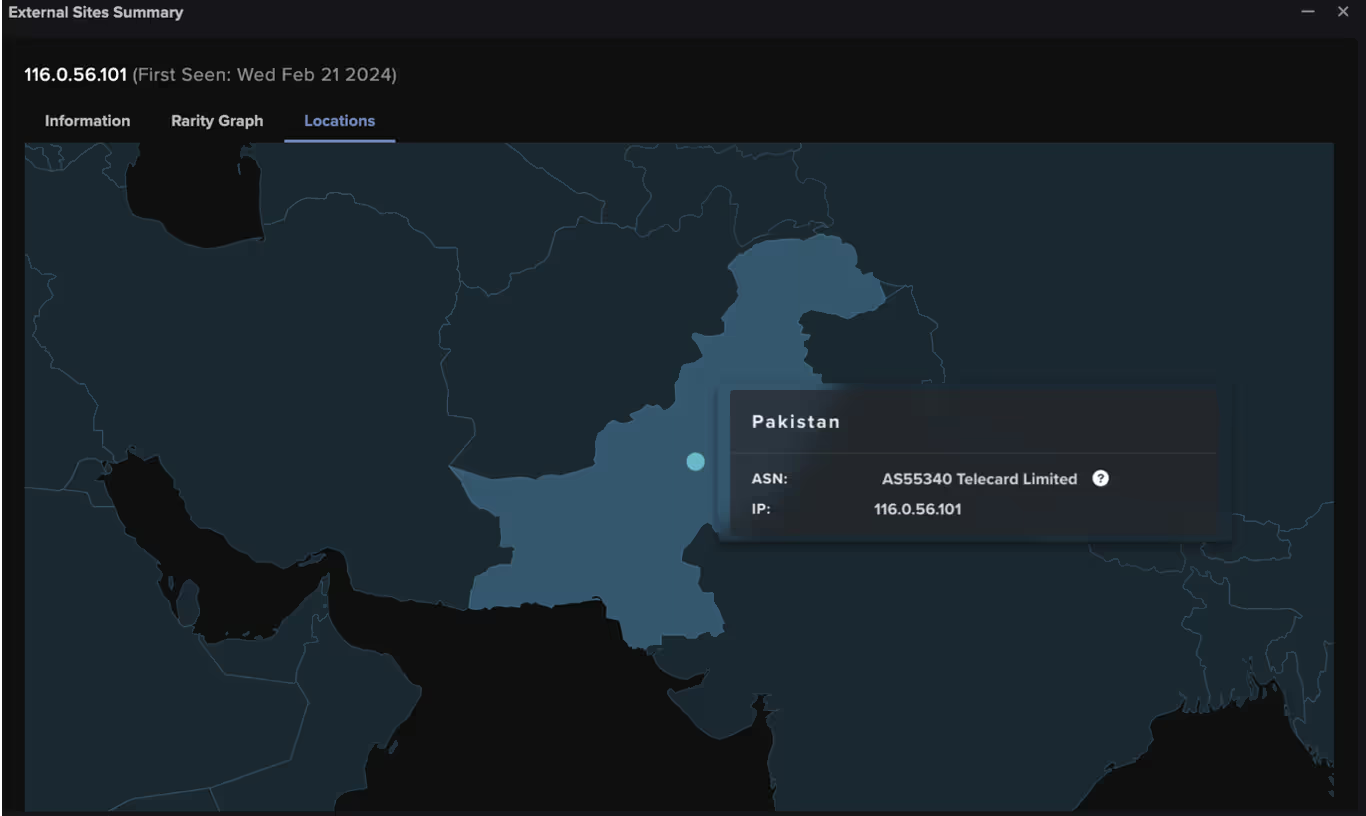
In one customer environment, Darktrace’s detection of post-exploitation activity began with the same indicators of ScreenConnect usage, including connections to screenconnect[.]com via port 8041, followed by connections to unusual domains flagged as malicious by OSINT, in this case 116.0.56[.]101 [16] [17]. However, on this deployment Darktrace also observed threat actors downloading a suspicious AnyDesk installer from the endpoint with the URI “hxxp[:]//116.0.56[.]101[:]9191/images/Distribution.exe”.
![Figure 4: Darktrace DETECT model alert highlighting the download of an unusual executable file from 116.0.56[.]101.](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/663e671300e1a5b26483fcea_Screenshot%202024-05-10%20at%2011.27.20%20AM.avif)
Further investigation by Darktrace’s Threat Research team revealed that this endpoint was associated with threat actors exploiting CVE-2024-1708 and CVE-2024-1709 [1]. Darktrace was additionally able to identify that, despite the customer being based in the United Kingdom, the file downloaded came from Pakistan. Darktrace recognized that this represented a deviation from the device’s expected pattern of activity and promptly alerted for it, bringing it to the attention of the customer.
Darktrace’s Autonomous Response
In this instance, the customer had Darktrace enabled in autonomous response mode and the post-exploitation activity was swiftly contained, preventing the attack from escalating.
As soon as the suspicious AnyDesk download was detected, Darktrace RESPOND applied targeted measures to prevent additional malicious activity. This included blocking connections to 116.0.56[.]101 and “*.56.101”, along with blocking all outgoing traffic from the device. Furthermore, RESPOND enforced a “pattern of life” on the device, restricting its activity to its learned behavior, allowing connections that are considered normal, but blocking any unusual deviations.

![Figure 7: Darktrace RESPOND blocking connections to the suspicious endpoint 116.0.56[.]101 and “*.56.101” following the download of the suspicious AnyDesk installer.](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/663e67ff976d5b71245b32a4_Screenshot%202024-05-10%20at%2011.31.17%20AM.avif)
The customer was later able to use RESPOND to manually quarantine the offending device, ensuring that all incoming and outgoing traffic to or from the device was prohibited, thus preventing any further malicious communication or lateral movement attempts.

Conclusion
In the observed cases of the ConnectWise ScreenConnect vulnerabilities being exploited across the Darktrace fleet, Darktrace was able to pre-emptively identify and contain network compromises from the onset, offering vital protection against disruptive cyber-attacks.
While much of the post-exploitation activity observed by Darktrace remained the same across different customer environments, important deviations were also identified suggesting that threat actors may be adapting their tactics, techniques and procedures (TTPs) from campaign to campaign.
While new vulnerabilities will inevitably surface and threat actors will continually look for novel ways to evolve their methods, Darktrace’s Self-Learning AI and behavioral analysis offers organizations full visibility over new or unknown threats. Rather than relying on existing threat intelligence or static lists of “known bads”, Darktrace is able to detect emerging activity based on anomaly and respond to it without latency, safeguarding customer environments whilst causing minimal disruption to business operations.
Credit: Emma Foulger, Principal Cyber Analyst for their contribution to this blog.
Appendices
Darktrace Model Coverage
DETECT Models
Compromise / Agent Beacon (Medium Period)
Compromise / Agent Beacon (Long Period)
Anomalous File / EXE from Rare External Location
Device / New PowerShell User Agent
Anomalous Connection / Powershell to Rare External
Anomalous Connection / New User Agent to IP Without Hostname
User / New Admin Credentials on Client
Device / New User Agent
Anomalous Connection / Multiple HTTP POSTs to Rare Hostname
Anomalous Server Activity / Anomalous External Activity from Critical Network Device
Compromise / Suspicious Request Data
Compliance / Remote Management Tool On Server
Anomalous File / Anomalous Octet Stream (No User Agent)
RESPOND Models
Antigena / Network::External Threat::Antigena Suspicious File Block
Antigena / Network::External Threat::Antigena File then New Outbound Block
Antigena / Network::Significant Anomaly::Antigena Enhanced Monitoring from Client Block
Antigena / Network::Significant Anomaly::Antigena Significant Anomaly from Client Block
Antigena / Network::Significant Anomaly::Antigena Controlled and Model Breach
Antigena / Network::Insider Threat::Antigena Unusual Privileged User Activities Block
Antigena / Network / External Threat / Antigena Suspicious File Pattern of Life Block
Antigena / Network / Insider Threat / Antigena Unusual Privileged User Activities Pattern of Life Block
List of IoCs
IoC - Type - Description + Confidence
185.62.58[.]132 – IP- IP linked with threat actors exploiting CVE-2024-1708 and CVE-2024-1709
108.61.210[.]72- IP - IP linked with threat actors exploiting CVE-2024-1708 and CVE-2024-1709
116.0.56[.]101 - IP - IP linked with threat actors exploiting CVE-2024-1708 and CVE-2024-1709
/MyUserName_ DEVICEHOSTNAME – URI - URI linked with threat actors exploiting CVE-2024-1708 and CVE-2024-1709
/images/Distribution.exe – URI - URI linked with threat actors exploiting CVE-2024-1708 and CVE-2024-1709
24780657328783ef50ae0964b23288e68841a421 - SHA1 Filehash - Filehash linked with threat actors exploiting CVE-2024-1708 and CVE-2024-1709
a21768190f3b9feae33aaef660cb7a83 - MD5 Filehash - Filehash linked with threat actors exploiting CVE-2024-1708 and CVE-2024-1709
MITRE ATT&CK Mapping
Technique – Tactic – ID - Sub-technique of
Web Protocols - COMMAND AND CONTROL - T1071.001 - T1071
Web Services - RESOURCE DEVELOPMENT - T1583.006 - T1583
Drive-by Compromise - INITIAL ACCESS - T1189 – NA
Ingress Tool Transfer - COMMAND AND CONTROL - T1105 - NA
Malware - RESOURCE DEVELOPMENT - T1588.001- T1588
Exploitation of Remote Services - LATERAL MOVEMENT - T1210 – NA
PowerShell – EXECUTION - T1059.001 - T1059
Pass the Hash - DEFENSE EVASION, LATERAL MOVEMENT - T1550.002 - T1550
Valid Accounts - DEFENSE EVASION, PERSISTENCE, PRIVILEGE ESCALATION, INITIAL ACCESS - T1078 – NA
Man in the Browser – COLLECTION - T1185 - NA
Exploit Public-Facing Application - INITIAL ACCESS - T1190 - NA
Exfiltration Over C2 Channel – EXFILTRATION - T1041 – NA
IP Addresses – RECONNAISSANCE - T1590.005 - T1590
Remote Access Software - COMMAND AND CONTROL - T1219 – NA
Lateral Tool Transfer - LATERAL MOVEMENT - T1570 – NA
Application Layer Protocol - COMMAND AND CONTROL - T1071 – NA
References:
[1] https://unit42.paloaltonetworks.com/connectwise-threat-brief-cve-2024-1708-cve-2024-1709/
[3] https://www.huntress.com/blog/a-catastrophe-for-control-understanding-the-screenconnect-authentication-bypass
[4] https://www.speedguide.net/port.php?port=8041
[5] https://www.connectwise.com/company/announcements/labtech-now-connectwise-automate
[6] https://www.connectwise.com/solutions/software-for-internal-it/automate
[7] https://www.securityweek.com/slashandgrab-screenconnect-vulnerability-widely-exploited-for-malware-delivery/
[8] https://arcticwolf.com/resources/blog/cve-2024-1709-cve-2024-1708-follow-up-active-exploitation-and-pocs-observed-for-critical-screenconnect-vulnerabilities/https://success.trendmicro.com/dcx/s/solution/000296805?language=en_US&sfdcIFrameOrigin=null
[9] https://www.connectwise.com/company/trust/security-bulletins/connectwise-screenconnect-23.9.8
[10] https://socradar.io/critical-vulnerabilities-in-connectwise-screenconnect-postgresql-jdbc-and-vmware-eap-cve-2024-1597-cve-2024-22245/
[11] https://www.trendmicro.com/en_us/research/24/b/threat-actor-groups-including-black-basta-are-exploiting-recent-.html
[12] https://otx.alienvault.com/indicator/ip/185.62.58.132
[13] https://www.virustotal.com/gui/ip-address/185.62.58.132/community
[14] https://www.virustotal.com/gui/ip-address/108.61.210.72/community
[15] https://otx.alienvault.com/indicator/ip/108.61.210.72
[16] https://www.virustotal.com/gui/ip-address/116.0.56[.]101/community
[17] https://otx.alienvault.com/indicator/ip/116.0.56[.]101







































