Darktrace recently detected a new technique used by threat actors to deliver malicious email payloads. The malicious link was observed hidden within a legitimate domain, namely Google Translate services. To understand its abusive capabilities, it is important to first understand a benign case of how these links are created.
Google often provides a ‘Translate this page’ option for sites written in a different language to the default browser language.
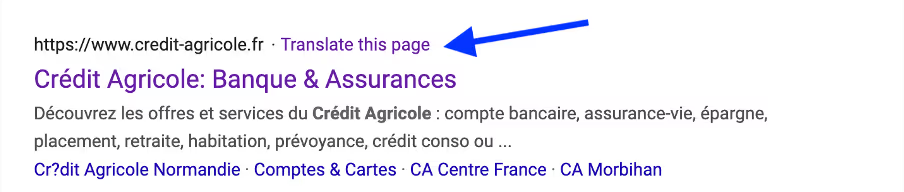
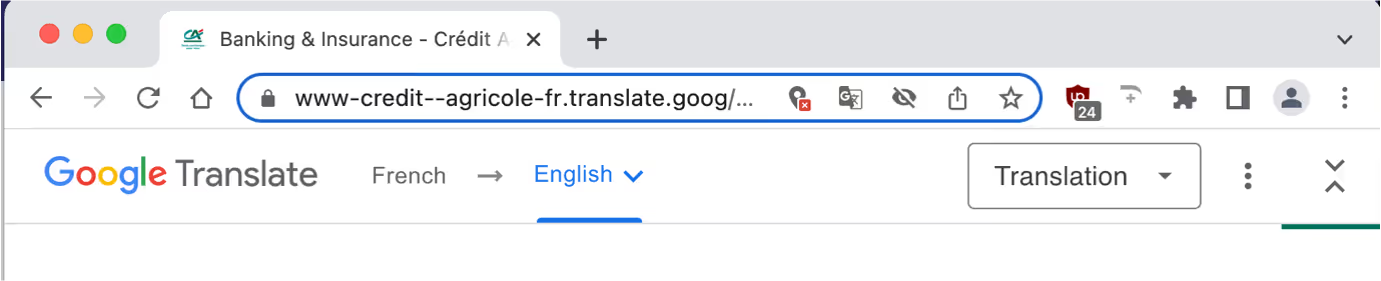
When this feature is exploited by threat actors it can be particularly dangerous, as legacy security products that rely on ‘known’ or ‘safe’ domain-based detection are likely to register these emails as safe and provide no protective actions. If a recipient were to click on the malicious link, they could risk losing their credentials or even compromising their machine.
In contrast, Darktrace/Email has been able to consistently identify and action emails from such campaigns. This blog will discuss one of these events.
The Campaign
The apparent motive in this attack was to harvest credentials and/or deploy malware on the recipient’s device. Credential harvesting can lead to the sale of credentials on the dark web, or the attacker may choose to leverage those credentials in subsequent attacks. Both harvesting credentials and deploying malware have severe potential ramifications, including but not limited to sensitive company data leaks and financial loss.
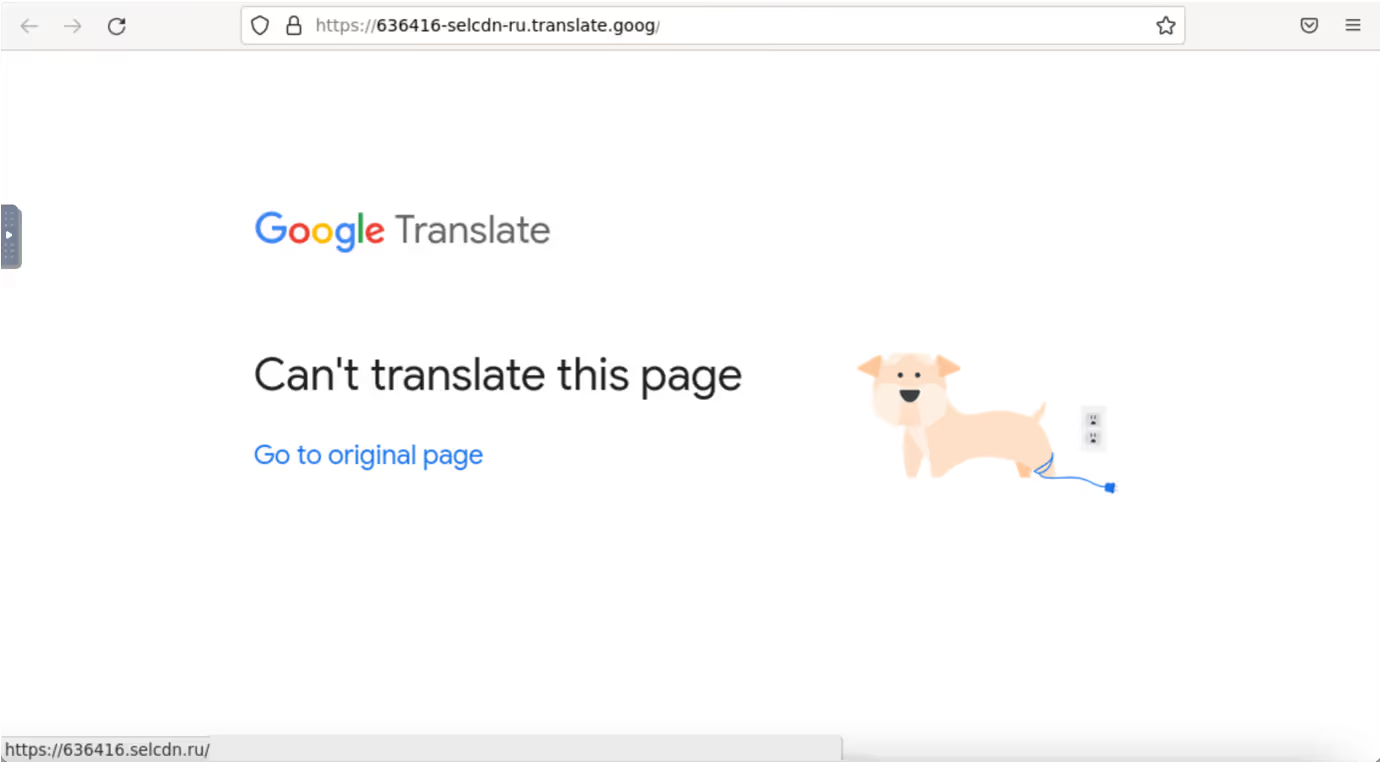
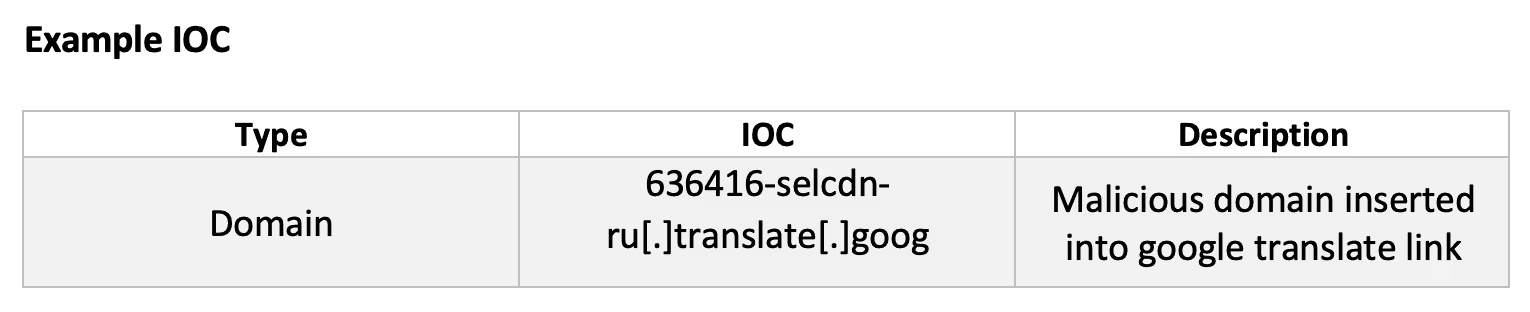
During this attack, the threat actor sent similar emails to a group of recipients in a short space of time. The recipients were not normally associated with each other and Darktrace swiftly identified them as unsolicited bulk mail. The new technique that was leveraged included using Google’s translate services to share malicious links using legitimate seeming domains. The malicious host was visible within the subdomain ‘636416-selcdn-ru[.]translate[.]goog’.
When clicked, the link displays a google translate page stating, “Can’t translate this page”. There is then a hyperlink, “Go to original page”, that brings the user to the malicious host- 636416[.]selcdn[.]ru. Finally, the host displays a fake webmail portal login. If a user engages, the attacker can harvest their credentials to either sell or use in subsequent attacks.
Darktrace Coverage
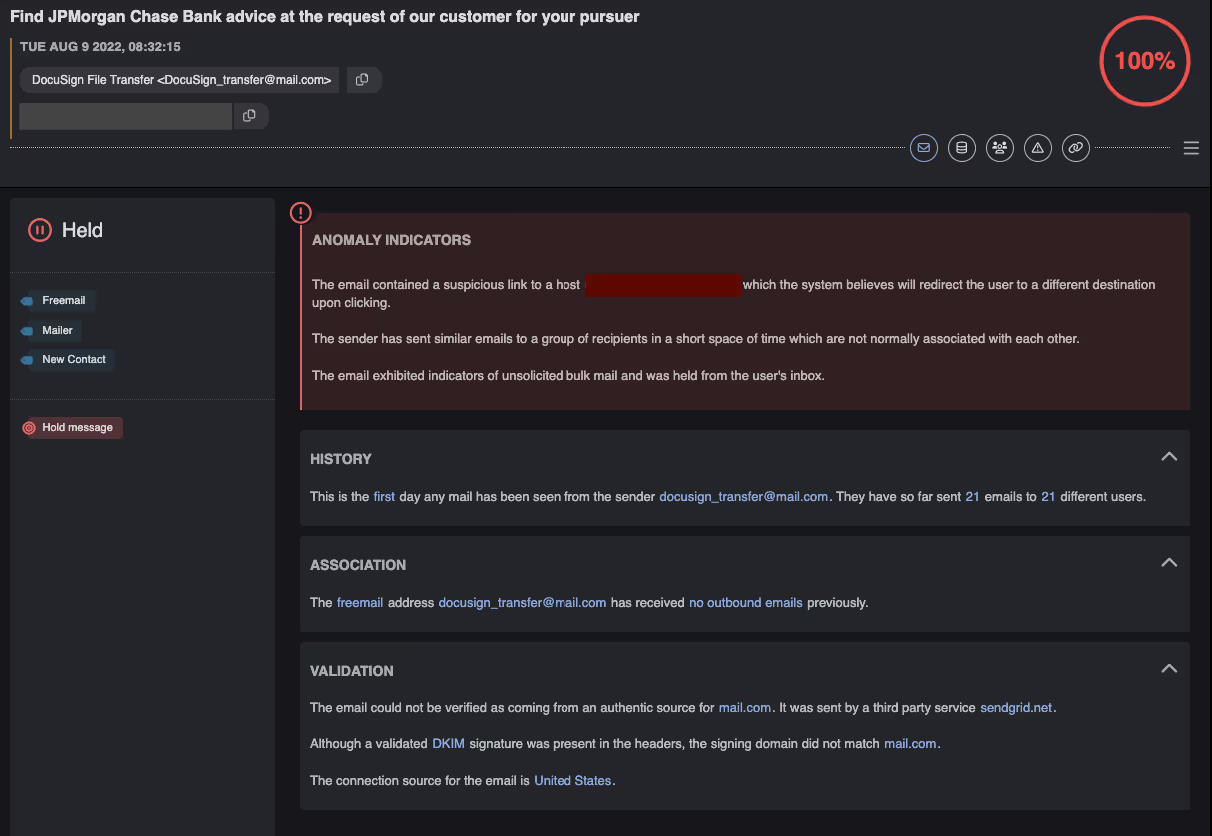
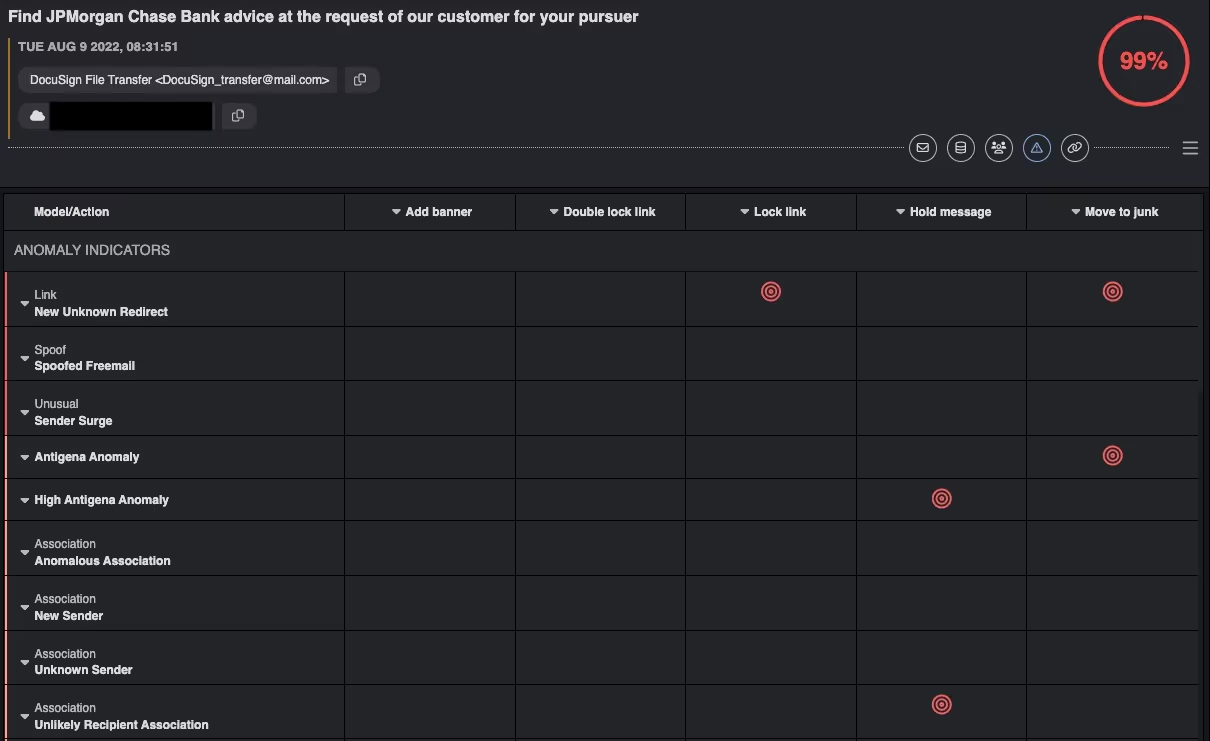
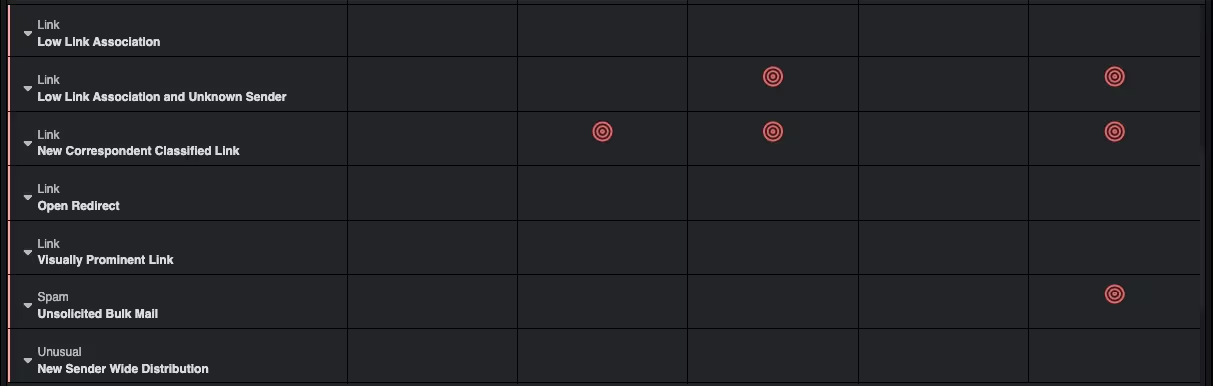
As the malicious emails contained links to ‘safe’ Google Translate domains, most email security products would not characterize the links as suspicious. However, Darktrace/Email levies hundreds of metrics to identify whether emails belong in a recipient’s inbox. In this case Darktrace highlighted anomalies including rare subdomains, links containing unknown redirects, emails from spoofed freemail accounts and senders that had sent a relatively large number of emails within a short time frame. Furthermore, the attacker had never sent any previous emails to the organization prior to this email campaign.
On top of providing visibility, the RESPOND function of Darktrace/Email took action autonomously and instantaneously without any human confirmation required. These actions included locking links and holding malicious emails.
Concluding Thoughts
Threat actors are continuously updating the way they deliver malicious payloads within emails. While this particular email campaign utilized Google Translate domains to hide malicious links, subsequent attacks may well be seen leveraging other legitimate domains. Companies are only as strong as their weakest link; a single compromised internal email account can be used to send phishing emails to internal recipients, collect sensitive company information, inject malware onto the device, and more. Security tools must evolve to focus on anomalies within the email, rather than relying on rules or signatures of previously seen attacks. Furthermore, email tools must be able to autonomously respond as soon as the malicious emails enter the company’s environment. Only with these precautions will the risks associated with malicious emails be mitigated.
Thanks to Steven Haworth and Steven Sosa for their contributions.
Appendices
Relevant Darktrace Model Detections
· Association / Anomalous Association
· Association / New Sender
· Association / Unknown Sender
· Association / Unlikely Recipient Association
· High Antigena Anomaly [part of the RESPOND functionality]
· Link / Low Link Association
· Link / Low Link Association and Unknown Sender
· Link / New Correspondent Classified Link
· Link / New Unknown Redirect
· Link / Open Redirect
· Link / Visually Prominent Link
· Spam / Unsolicited Bulk Mail
· Spoof / Spoofed Freemail
· Unusual / New Sender Wide Distribution
· Unusual / Sender Surge














.avif)


.avif)






![Pivoting off the previous event by filtering the timeline to events within the same window using timestamp: [“2026-02-18T09:09:00Z” TO “2026-02-18T09:12:00Z”].](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/69a8a18526ca3e653316a596_Screenshot%202026-03-04%20at%201.17.50%E2%80%AFPM.png)


