Trusted relationships between organizations and third parties have become an increasingly popular target for cyber threat actors to gain access to sensitive networks. These relationships are typically granted by organizations to external or adjacent entities and allow for the access of internal resources for business purposes.1 Trusted network relations can exist between constituent elements of an overarching corporation, IT-service providers and their customers, and even implicitly between IT product vendors and their customers.
Several high-profile compromises have occurred due to the leveraging of privileged network access by such third parties. One prominent example is the 2016 DNC network attack, in which the trust between the Democratic Congressional Campaign Committee (DCCC) and the Democratic National Committee (DNC) was exploited. Supply chain attacks, which also leverage the implicit trust between IT vendors and customers, are also on the rise with some estimates projecting that by 2025, almost half of all organizations will be impact by supply chain compromises.2 These trends may also be attributed to the prevalence of remote work as well as the growth in IT-managed service providers.3
Given the nature of such network relationships and threat techniques, signatures-based detection is heavily disadvantaged in the identification and mitigation of such trust abuses; network administrators cannot as easily use firewalls to block IPs that need access to networks. However, Darktrace DETECT™, and its Self-Learning AI, has proven successful in the identification and mitigation of these compromises. In September 2023, Darktrace observed an incident involving the abuse of such a trusted relationship on the network of a healthcare provider.
Attack Overview
In early September 2023, a Darktrace customer contacted the Darktrace Security Operations Center (SOC) through the Ask the Expert™ (ATE) service requesting assistance with suspicious activity detected on their network. Darktrace had alerted the customer’s security team to an unknown device that had appeared on their network and proceeded to perform a series of unexpected activities, including reconnaissance, lateral movement, and attempted data exfiltration.
Unfortunately for this customer, Darktrace RESPOND™ was not enabled in autonomous response mode at the time of this compromise, meaning any preventative actions suggested by RESPOND had to be applied manually by the customer’s security team after the fact. Nevertheless, Darktrace’s prompt identification of the suspicious activity and the SOC’s investigation helped to disrupt the intrusion in its early stages, preventing it from developing into a more disruptive compromise.
Initial Access
Darktrace initially observed a new device that appeared within the customers internal network with a Network Address Translated (NAT) IP address that suggested remote access from a former partner organization’s network. Further investigation carried out by the customer revealed that poor credential policies within the partner’s organization had likely been exploited by attackers to gain access to a virtual desktop interface (VDI) machine.
Using the VDI appliance of a trusted associate, the threat actor was then able to gain access to the customer’s environment by utilizing NAT remote access infrastructure. Devices within the customer’s network had previously been utilized for remote access from the partner network when such activity was permitted and expected. Since then, access to this network was thought to have been removed for all parties. However, it became apparent that the remote access functionality remained operational. While the customer also had firewalls within the environment, a misconfiguration at the time of the attack allowed inbound port access to the remote environment resulting in the suspicious device joining the network on August 29, 2023.
Internal Reconnaissance
Shortly after the device joined the network, Darktrace observed it carrying out a string of internal reconnaissance activity. This activity was initiated with internal ICMP address connectivity, followed by internal TCP connection attempts to a range of ports associated with critical services like SMB, RDP, HTTP, RPC, and SSL. The device was also detected attempting to utilize privileged credentials, which were later identified as relating to a generic multi-purpose administrative account. The threat actor proceeded to conduct further internal reconnaissance, including reverse DNS sweeps, while also attempting to use six additional user credentials.
In addition to the widespread internal connectivity, Darktrace observed persistent connection attempts focused on the RDP and SMB protocols. Darktrace also detected additional SMB enumeration during this phase of the attacker’s reconnaissance. This reconnaissance activity largely attempted to access a wide variety of SMB shares, previously unseen by the host to identify available share types and information available for aggregation. As such, the breach host conducted a large spike in SMB writes to the server service (srvsvc) endpoint on a range of internal hosts using the credential: extramedwb. SMB writes to this endpoint traditionally indicate binding attempts.
Beginning on August 31, Darktrace identified a new host associated with the aforementioned NAT IP address. This new host appeared to have taken over as the primary host conducting the reconnaissance and lateral movement on the network taking advantage of the VDI infrastructure. Like the previous host, this one was observed sustaining reconnaissance activity on August 31, featuring elevated SMB enumeration, SMB access failures, RDP connection attempts, and reverse DNS sweeps. The attackers utilized several credentials to execute their reconnaissance, including generic and possibly default administrative credentials, including “auditor” and “administrator”.
Following these initial detections by Darktrace DETECT, Darktrace’s Cyber AI Analyst™ launched an autonomous investigation into the scanning and privileged internal connectivity and linked these seemingly separate events together into one wider internal reconnaissance incident.

Lateral Movement
Following the reconnaissance activity performed by the new host observed exploiting the remote access infrastructure, Darktrace detected an increase in attempts to move laterally within the customer’s network, particularly via RPC commands and SMB file writes.
Specifically, the threat actor was observed attempting RPC binds to several destination devices, which can be used in the calling of commands and/or the creation of services on destination devices. This activity was highlighted in repeated failed attempts to bind to the ntsvcs named pipe on several destination devices within the network. However, given the large number of connection attempts, Darktrace did also detect a number of successful RPC connections.
Darktrace also detected a spike in uncommon service control (SVCCTL) ExecMethod, Create, and Start service operations from the breach device.
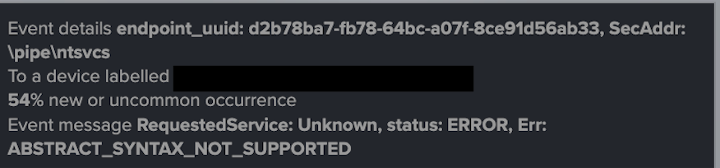
Additional lateral movement activity was performed using the SMB/NTLM protocols. The affected device also conducted a series of anonymous NTLM logins, whereby NTLM authentication attempts occurred without a named client principal, to a range of internal hosts. Such activity is highly indicative of malicious or unauthorized activity on the network. The host also employed the outdated SMB version 1 (SMBv1) protocol during this phase of the kill chain. The use of SMBv1 often represents a compliance issue for most networks due to the high number of exploitable vulnerabilities associated with this version of the protocol.
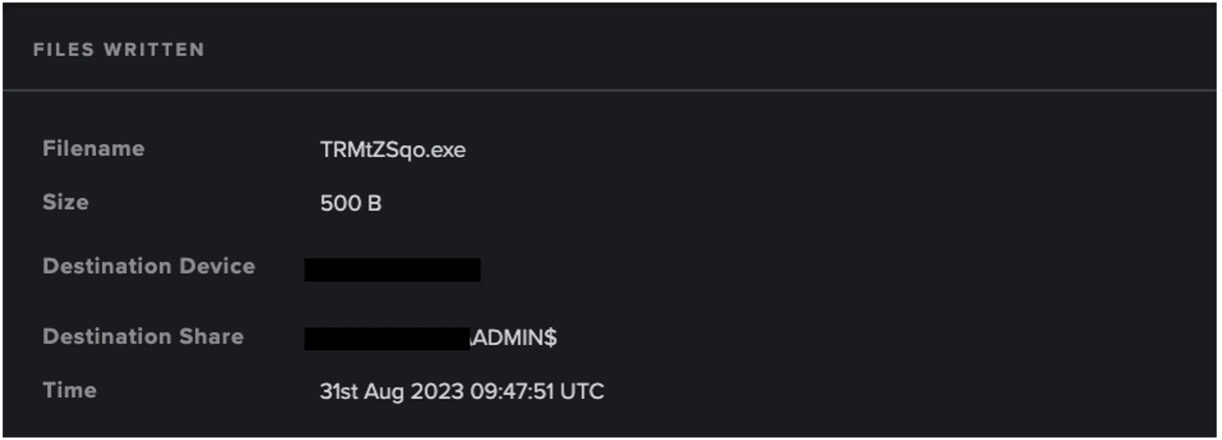
Lastly, Darktrace identified the internal transfer of uncommon executables, such as ‘TRMtZSqo.exe’, via SMB write. The breach device was observed writing this file to the hidden administrative share (ADMIN$) on a destination server. Darktrace recognized that this activity was highly unusual for the device and may have represented the threat actor transferring a malicious payload to the destination server for further persistence, data aggregation, and/or command and control (C2) operations. Further SMB writes of executable files, and the subsequent delete of these binaries, were observed from the device at this time. For example, the additional executable ‘JAqfhBEB.exe’ was seen being deleted by the breach device. This deletion, paired with the spike in SVCCTL Create and Start operations occurring, suggests the transfer, execution, and removal of persistence and data harvesting binaries within the network.
Conclusion
Ultimately, Darktrace was able to successfully identify and alert for suspicious activity being performed by a threat actor who had gained unauthorized access to the customer’s network by abusing one of their trusted relationships.
The identification of scanning, RPC commands and SMB sessions directly assisted the customer in their response to contain and mitigate this intrusion. The investigation carried out by the Darktrace SOC enabled the customer to promptly triage and remediate the attack, mitigating the potential damage and preventing the compromise from escalating further. Had Darktrace RESPOND been enabled in autonomous response mode at the time of the attack, it would have been able to take swift action to inhibit the scanning, share enumerations and file write activity, thereby thwarting the attacker’s network reconnaissance and lateral movement attempts.
By exploiting trusted relationships between organizations, threat actors are often able to bypass traditional signatured-based security methods that have previously been reconfigured to allow and trust connections from and to specific endpoints. Rather than relying on the configurations of specific rules and permitted IP addresses, ports, and devices, Darktrace DETECT’s anomaly-based approach to threat detection meant it was able to identify suspicious network activity at the earliest stage, irrespective of the offending device and whether the domain or relationship was trusted.
Credit to Adam Potter, Cyber Security Analyst, Taylor Breland, Analyst Team Lead, San Francisco.
Darktrace DETECT Model Breach Coverage:
- Device / ICMP Address Scan
- Device / Network Scan
- Device / Suspicious SMB Scanning Activity
- Device / RDP Scan
- Device / Possible SMB/NTLM Reconnaissance
- Device / Reverse DNS Sweep
- Anomalous Connection / SMB Enumeration
- Device / Large Number of Model Breaches
- Anomalous Connection / Suspicious Activity On High Risk Device
- Unusual Activity / Possible RPC Recon Activity
- Device / Anonymous NTLM Logins
- Anomalous Connection / Unusual SMB Version 1 Connectivity
- Device / Repeated Unknown RPC Service Bind Errors
- Anomalous Connection / New or Uncommon Service Control
- Compliance / SMB Drive Write
- Anomalous File / Internal / Unusual Internal EXE File Transfer
- Device / Multiple Lateral Movement Model Breaches
AI Analyst Incidents:
- Scanning of Multiple Devices
- Extensive Unusual RDPConnections
- SMB Write of Suspicious File
- Suspicious DCE-RPC Activity
MITRE ATT&CK Mapping
- Tactic: Initial Access
- Technique: T1199 - Trusted Relationship
- Tactic: Discovery
- Technique:
- T1018 - Remote System Discovery
- T1046 - Network Service Discovery
- T1135 - Network Share Discovery
- T1083 - File and Directory Discovery
- Tactic: Lateral Movement
- Technique:
- T1570 - Lateral Tool Transfer
- T1021 - Remote Services
- T1021.002 - SMB/Windows Admin Shares
- T1021.003 - Distributed Component Object Model
- T1550 - Use Alternate Authentication Material
References
1https://attack.mitre.org/techniques/T1199/
2https://www.cloudflare.com/learning/insights-supply-chain-attacks/


















