Shining a light into the murky world of industrial cyber security — where major incidents can be kept hush, and information is often not made publicly available — the SANS Institute held its 16th annual ICS Security Summit in March. With virtual events across APAC, EMEA, and the US, the round-the-clock summit stressed the importance of having good visibility and a strong understanding of industrial networks for anomaly detection and incident response. Speakers at the event also emphasized how automation can be used in industrial security to address budget restraints and skill shortages.
The summit also detailed the direction of developments in both industrial technologies and the surrounding threat landscape, including the adoption of cloud technologies for Industrial Control Systems, the broadening scope of threat actors, and the inherent limitations of patching and vulnerability management.
In addition to framing the key points of the summit, this blog will hone in on the program’s most salient points: namely, how building an in-depth understanding of ‘self’ for an ICS ecosystem can help fend off the rising tide of threat actors, and at the same time allow organizations to embrace new technologies in the face of their associated risks. Ultimately, by ‘knowing thyself,’ organizations will be able to simultaneously fight external threats, and also gain visibility into new areas of vulnerability that arise inside an organization as it evolves its industrial environment.
SANS Summit 2021: An overview
The following provides a high-level overview of the major topics discussed throughout the SANS summit:
Attacker TTPs
Threat Trend: MITRE ATT&CK for ICS provides details of known attack tradecraft.
Industry Challenge: There has been a historic lack of sharing lessons learned within the community.
Recommendation: Understand attack TTPs and align your defences with those techniques.
Industry Trend: MITRE ATT&CK for ICS offers a big step forward for the community to learn from previous attacks.
Visibility
Threat Trend: The SolarWinds attack has emphasized the vulnerability of ICS e.g. exploiting SNMP communications in BMS.
Industry Challenge: The absence of logging and event management has hindered SolarWinds investigations in CNI.
Recommendation: Use active network monitoring for log generation, and increase network and host visibility.
Industry Trend: The SolarWinds attack has emphasized the importance of CNI cyber security to the Biden administration.
Test your defenses
Threat Trend: Common TTPs — misuse of valid accounts, abuse of remote services, phishing/spear phishing.
Industry Challenge: Vulnerability tracking is not adequate to defend ICS networks — vulnerability reporting is far from comprehensive, and attackers are exploiting legitimate tools to gain access.
Recommendation: Test your defenses and your defenders using lab environments, external pentests, and adversary simulations.
Industry Trend: Pentesting of ICS environments is being performed remotely as a result of lockdown restrictions.
Know thyself
Threat Trend: The barrier to hacking ICS is lowering — threat actors are expanding, from nation states to cyber-criminals e.g. EKANS.
Industry Challenge: OT security teams suffer from a skills shortage and tight budgets.
Recommendation: Make use of the defender’s home turf advantages — defense-in-depth, learn ‘normal’ network behavior, gain visibility over internal comms.
Industry Trend: Digital solutions, such as cloud and virtualization, are being used to solve many ICS challenges.
New solutions bring new risks
Threat Trend: Third-party risks, such as OEMs and remote access points, are being exploited to gain direct access into ICS environments.
Industry Challenge: New digital solutions bring new challenges — supply chain risk, IT/OT convergence, compliance obligations, vendor lock-in.
Recommendation: If you can’t see the network, you can’t defend the network — improve visibility, identify crown jewels, boost incident response capability, and validate network segmentation.
Industry Trend: Renewable Energy industry is a big adopter of innovative ICS solutions, such as cloud, remote management, and ICSaaS. The decision to migrate to these solutions increasingly seems to be when, not if.
‘Know thyself’: Learning ‘self’ to identify emerging threats
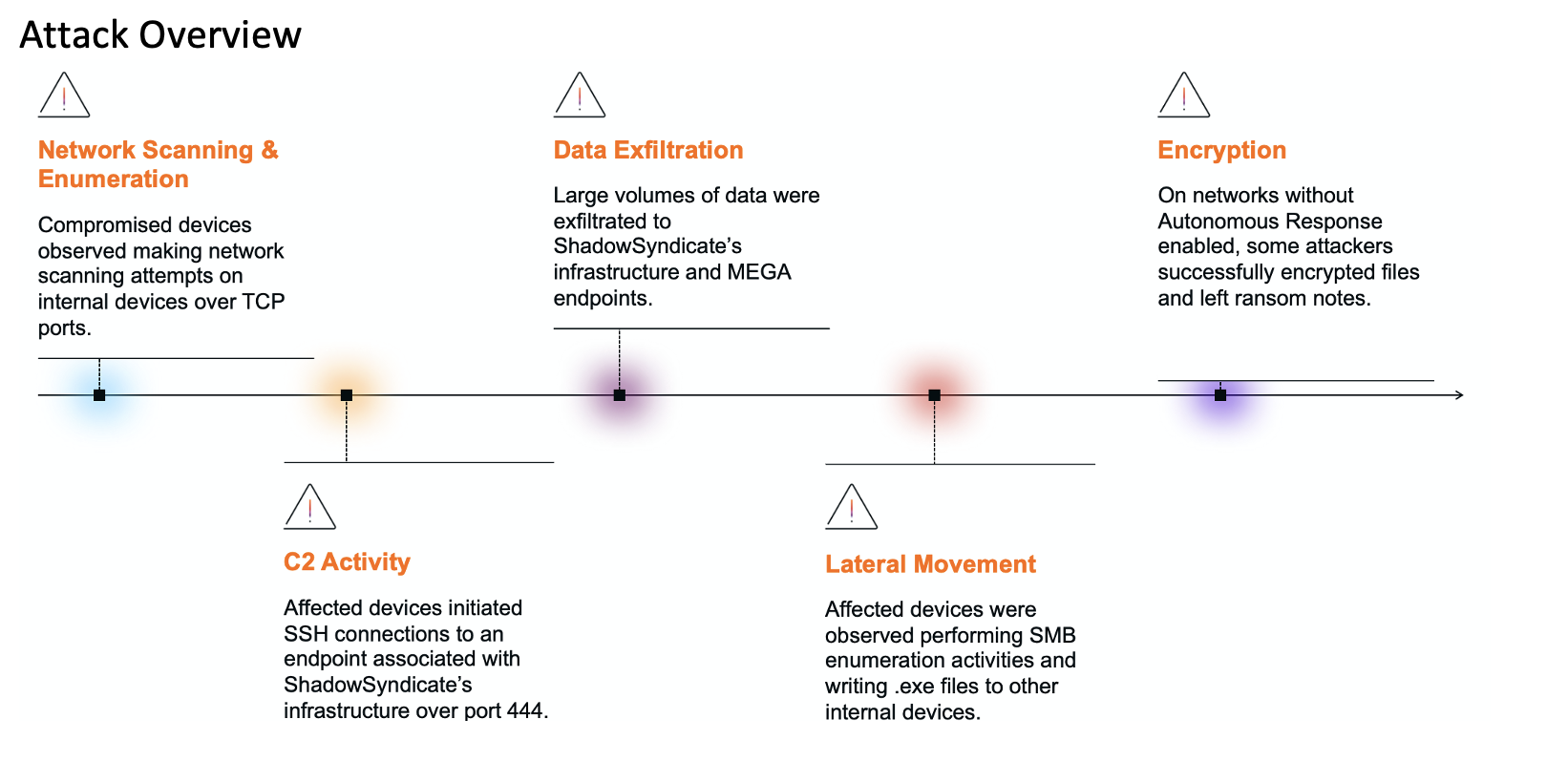
A wide variety of threat actors are making their debut in the global ICS threat landscape. First, new state-sponsored advanced persistant threat groups (APTs) are targeting industrial ecosystems every year. 2020 also saw the addition of organized crime groups targeting ICS with new ransomware strains such as EKANS.
Accordingly, cyber-attacks on industrial systems are no longer the sole domain of nation states. With ransomware-as-a-service becoming increasingly available on the Dark Web, the barrier of entry for attacking critical infrastructure and manufacturing is demonstrably lowering. In light of this, experts at the SANS conference recommend gaining a detailed understanding of your network and making use of the defender’s home advantage with defence-in-depth.
With attacks growing in scale and sophistication, there is a growing recognition that defenses that sit at the border of organizations and attempt to keep threats out are no longer enough. Organizations must move to a model that assumes a breach, and adopt technologies that can identify cyber-threats once they are inside. This can only be achieved with a real-time, granular understanding of ‘normal’ behavior for every device and controller.
By learning, from scratch, the normal ‘pattern of life’ for all devices, users, and peer groups across industrial networks, Darktrace’s Industrial Immune System builds a sense of self for everything seen in an ICS ecosystem, as well as the digital environment as a whole. In this way, Darktrace allows organizations to ‘know thyself’ to a unparalleled degree, building a dynamic understanding of normal rather than relying on static baselines.
New solutions bring new risks
Throughout the summit, speakers discussed how they have used digital solutions such as cloud and virtualization to solve problems and cut costs. In particular, the renewable energy sector is a big adopter of cloud solutions, or “ICS as a Service” (ICSaaS). A wind farm in California, for example, might be remotely controlled by engineers on the east coast, or a vendor might maintain and run equipment for a hydroelectric plant in Latin America from their European headquarters.
As customers move to adopt these kinds of digital solutions — and with these decisions typically being made at board-level, rather than by the engineers — it seems more a question of when, not if, we see wider adoption of these technologies in the ICS community.
As OT converges with IT in the cloud, so do their associated risks. These new risks create headwinds to change, but some sectors are still adopting these new solutions and making big savings. Unified visibility across IT, OT, and the cloud have thus become a necessity for organizations seeking to accelerate digital transformation while also managing the risks of digitization and of their increasingly dynamic workforces.
A changing landscape
In the face of a new era of cyber-threats, the focus for OT specialists should not be on reactive measures, but embracing new self-learning technologies that develop an evolving understanding of ‘normal’ across industrial systems, the corporate network, cloud environments, and beyond.
By adapting to changes in the digital infrastructure, AI-powered defenses can detect and respond to zero-day threats, while alleviating the burden of security teams by automating much of the manual processes required in post-incident investigation. And by unifying insights across a range of different technologies, organizations can benefit from an enterprise-wide approach to security rather than relying on siloed defenses that lack the context for accurate decision-making.
In this age of advanced cyber-criminal rings and state-sponsored attacks, critical infrastructure and other industrial environments are now the focal point for cyber espionage and intrusions seeking to disrupt operations. The SANS ICS Security Summit reminds us of the need for defenders to face this new landscape with new and adaptive technologies that can disrupt the early signs of a threat, whether known or unknown.
Thanks to Darktrace analyst Oakley Cox for his insights.