The following guest-authored blog post examines how Cyberseer detected highly advanced red team activities with Darktrace’s Enterprise Immune System.
At Cyberseer, a managed security provider, our analysts know that thwarting sophisticated cyber-criminals requires being prepared for any eventuality. A red team attack today could easily be replicated by far less benign actors tomorrow, which is why we treat these exercises with the same gravity we would a genuine threat, employing the world’s most advanced AI cyber defenses like Darktrace to leave the bad guys without anywhere to hide.
Recently, one of our customers was involved in a red team assessment, partly as a means to see how their security team would react and contain the attack, and partly to determine the visibility of the different attack techniques across their security stack. During the engagement, the red team leveraged a number of stealthy “Living off the Land” (LotL) techniques. LotL refers to the malicious use of legitimate tools present on a system — such as PowerShell scripting, WMI, or PsExec — in order to execute attacks. It should be noted that these techniques are not just limited to red teamers: threat-actors are making use of such tools on compromised systems, a notable example being the 2017 Petya/NotPetya attack.
Here’s an example of how Cyberseer’s analysts used Darktrace to detect the red team, without prior knowledge of their techniques, in real time:
Invoke — Bloodhound
Created by professional penetration tester Andy Robbins, Bloodhound is an open source tool that uses graph theory to understand the relationships in an Active Directory (AD) environment. It can be harnessed to quickly gain deep insights into AD by enumerating all the computers for which a given user has admin rights, in addition to ascertaining group membership information. In the right hands, security teams can use Bloodhound to identify and then limit attack vectors. In the wrong hands, attackers can easily exploit these same pathways if left unaddressed.
To collect data, Bloodhound is complemented by a data ingestor called Sharphound, which comes either as a PowerShell script or an executable. Sharphound makes use of native Windows APIs to query and retrieve information from target hosts. For example, to enumerate Local Admin users, it calls ‘NetLocalGroupGetMember’ API to interact with the Security Account Manager (SAM) database file on the remote host.
These tools typically produce a number of artifacts that we would expect to see from the host device within network traffic:
- Increase in connections to LDAP (389) and SMB (445) ports
- Increase in connections to IPC$ shares
- Increase in Distributed Computing Environment / Remote Procedure Calls (DCE_RPC) Connections to the following named pipes:
- \PIPE\wkssvc - Query logged-in users
- \PIPE\srvsvc - Query system information
- \PIPE\svcctl - Query services with stored credentials
- \PIPE\atsvc - Query scheduled tasks
- \PIPE\samr - Enumerate domain and user information
- \PIPE\lsass - Extract credential information
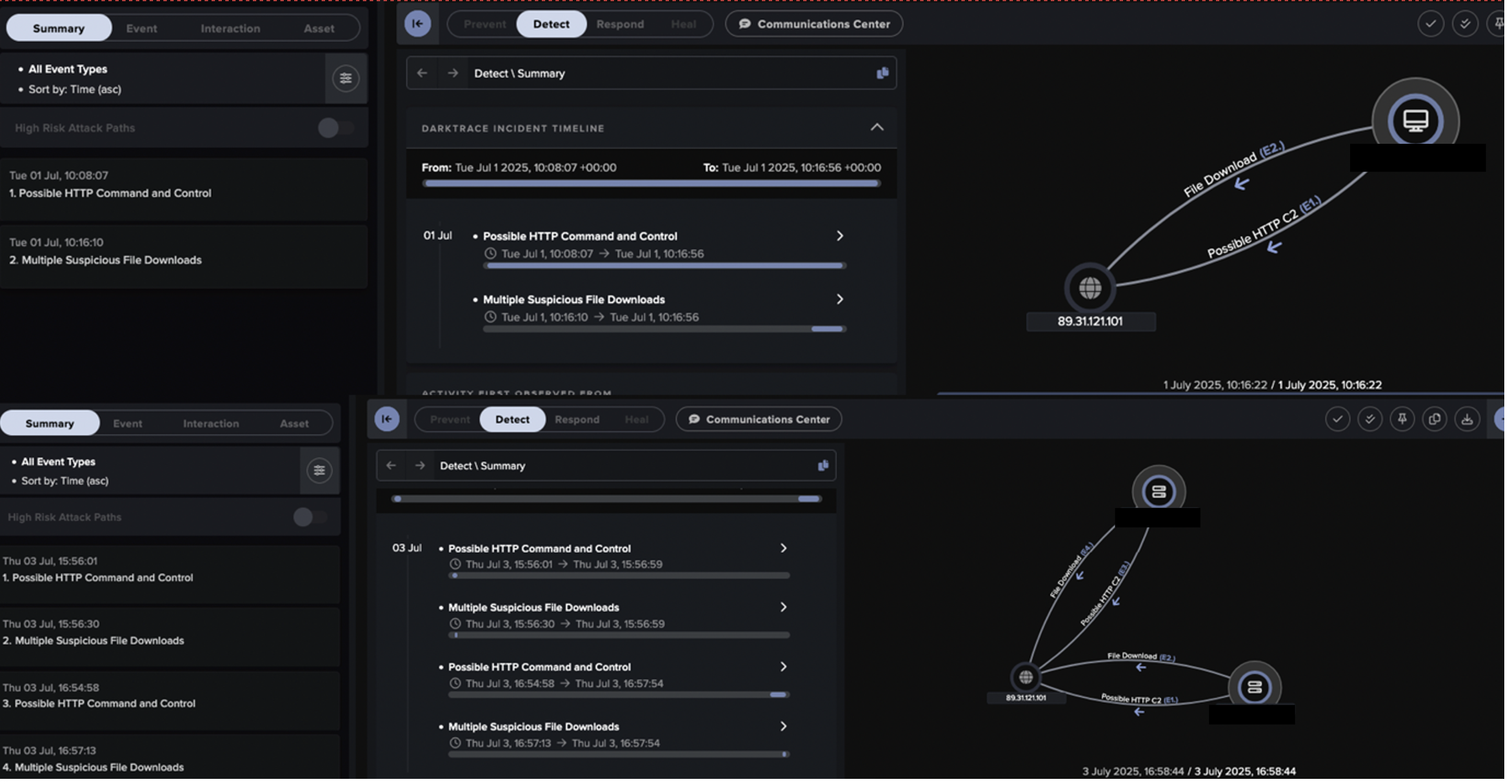
Associating this back to the red team engagement, upon execution of the Bloodhound tool the attacking device began reaching out to a large number of internal devices, causing a spike in internal connections:
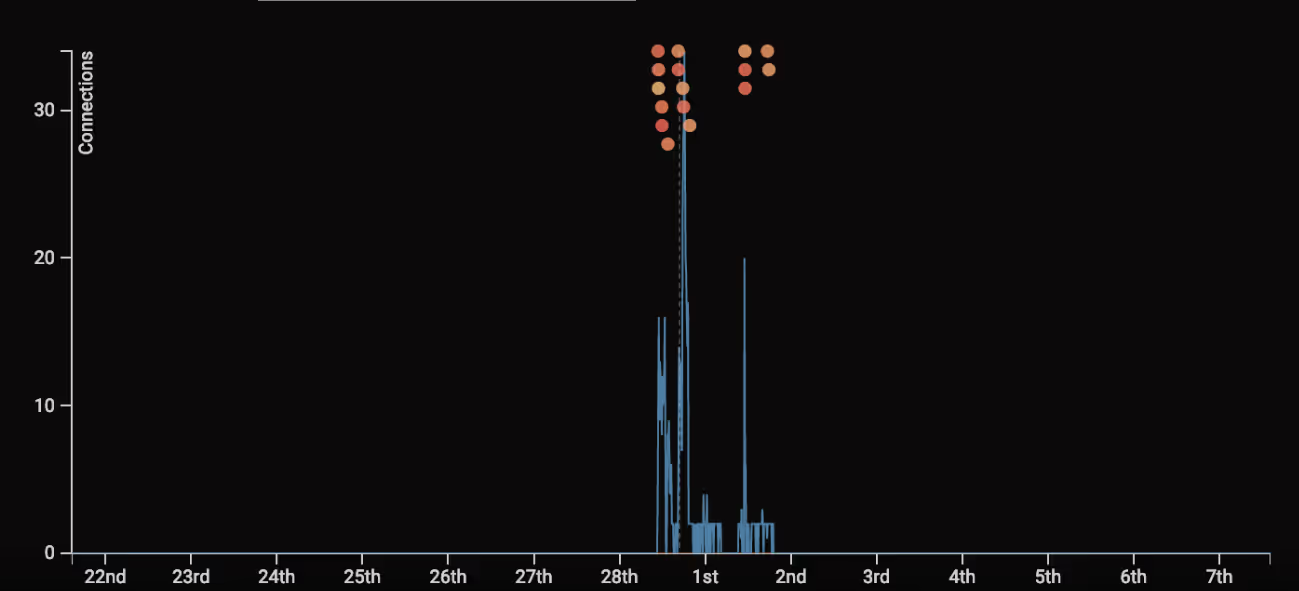
Figure 1: Darktrace visualizing the increase in internal connections, with each dot representing a unique model breach triggered by Bloodhound activity.
In fact, the large volume of anomalous connections triggered a number of Darktrace’s behavioral models, including:
- Anomalous Connection / SMB Enumeration
- Anomalous Connection / New Service Control
- Device / Network Scan
- Device / Expanded Network Scan
- Unusual Activity / Unusual Activity from Multiple Metrics
- Unusual Activity / Sustained Suspicious Activity
- Unusual Activity / Sustained Unusual Activity
Drilling deeper into these connections, it was possible to identify the named \PIPE\ connections that were detailed above:
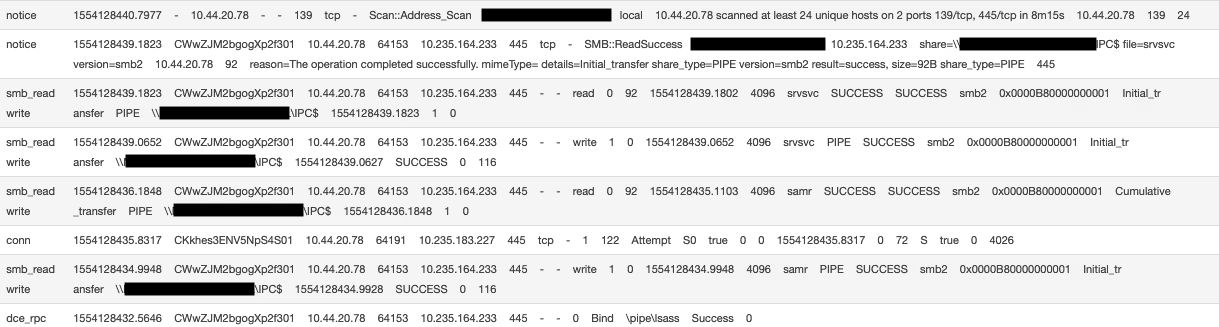
Figure 2: Reviewing the raw connection logs within Darktrace’s Advanced Search.
Looking from top to bottom, we see scanning of devices on ports 139 and 445, access to remote IPC$ shares, SMB read / writes of the srvsvc, and samr pipes and lsass binds. Although these protocols have legitimate applications within a typical network, a device initiating so many of them within a short time frame warrants further investigation.
Darktrace AI not only shined a light on these activities, it automatically determined that they were potentially threatening despite being benign under most circumstances. Rooted in an ever-evolving understanding of our customer’s normal ‘pattern of life’, Darktrace correlated numerous weak indicators of anomalous behavior to flag the activity as a significant risk within seconds.
Invoke — PasswordSpray
“Password spraying” is an attack that targets a large number of accounts with a few commonly used passwords. In this case, for instance, the red team attempted to brute-force access to a file share. Although this tactic may seem rudimentary, a recent study by the NCSC found that 75% of organizations had accounts with passwords that featured in the top 1,000 passwords, while 87% had accounts with passwords that featured in the top 10,000.
Similar to the previous Bloodhound attack, the password spraying attack began with an increase in SMB connections on port 445. Darktrace alerted to even this relatively small number of connections, since it was anomalous for our customer’s unique network:
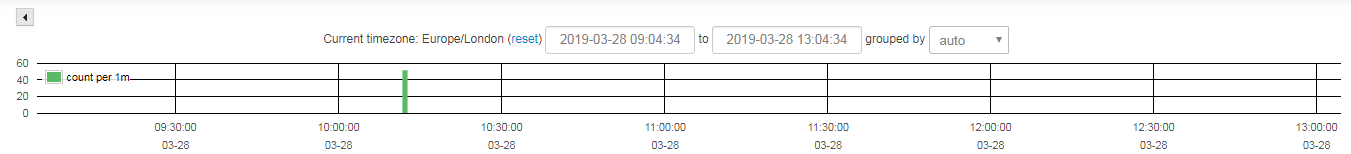
Figure 3: Volume of SMB session failures made to file shares from the attacker’s device.
Each of these connections was making use of a user credential and random password. From the logs below it is possible to see all of the SMB session failures:

Figure 4: A device event log showing repeated SMB session failures for each of the unsuccessful authentication attempts.
Even with only 50 total attempts seen, Darktrace quickly alerted upon both SMB enumeration and brute-force behaviors.
Both of these scenarios highlight the benefits of an AI-powered approach. Rather than focusing on hash or string matches for such tools, Darktrace is able to quickly identify anomalous patterns of behavior linked with their usage. This nuance is particularly critical in this case, given that all of these activities are not malicious in many situations. By differentiating between subtle threats and harmless traffic, Darktrace helps us defeat red teams and real criminals alike.